Advanced Window Manager is a potentially unwanted software that floods the user’s system with advertisements. Its pretends to be a tool that adds new functionality to Windows, but in fact redirects search queries, tracks user’s Internet activity and shows advertisements. Typical ways of this program distribution are software bundling and malvertising.
Advanced Window Manager Overview
Advanced Window Manager is an unwanted adware-like program. Despite positioning itself as a useful utility, its main task is to bombard the user with ads. At the same time, the program most often advertises fraudulent or malicious things, putting the user at serious risk. Clicking on the promotions that this Window Manager shows may redirect the user to a rogue website that inadvertently downloads other potentially unwanted software.

Another undeclared feature is collecting information about a user’s Internet activity. This data includes search queries, entered URLs, geodata, and IP addresses, which will then be sold to third parties. Advanced Window Manager is usually distributed as add-on software in bundles of other programs. Since the software is not very stealthy, the user can see the process (or several) in the Task Manager.
Detailed Analysis
Let’s analyze how Advanced Window Manager behaves in the system to understand its true nature. It arrives through the installer, that precedes the original program, and does some basic system check. During installation, the unwanted software extracts the following files to a temporary folder on the system:
C:\Users\Admin/AppData\Local\Temp\7zS4E1438CD\setup_install.exe
C:\Users\Admin/AppData\Local\Temp\7zS4E1438CD\libcurlpp.dll.
C:\Users/Admin/AppData/Local/Temp/7zS4E1438CD/libstdc++-6.dll.
C:\Users\Admin/AppData\Local\Temp\7zS4E1438CD\libcurl.dll.
It also resets some files, including:
%WINDIR%\Microsoft.NET\Framework\v4.0.30319\clr.dll
%WINDIR%\System32\rundll32.exe.
C:\Users\
C:\Users\
Installation
Once installed, Advanced Window Manager (sample on VirusTotal) starts performing its main task – flooding the user’s system with ads. It checks the following registry value, which is responsible for regionalizing the system to install more “relevant” programs.
\REGISTRY\USER\S-1-5-21-1346565761-3498240568-4147300184-1000\Control Panel\International\Geo\Nation
\REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IMM\Ime File
\Registry\Machine\Software\Policies\Microsoft\System\DNSclient
After that little check, the malware connects to its command server. In my case, one of the requests that followed the original connection installed an unwanted program called Ultra Media Burner. It most likely depends on the results of the aforementioned geolocation check.
GET http://limesfile.com
GET http://limesfile.com/Ea42LhC7KVL6GEpzgxwW/C_Net_8Rpjkd5GEqRYJq87/UltraMediaBurner.exe
GET http://estrix.xyz/addInstallImpression.php?key=125478824515ADNxu2ccbwe&ip=&oid=139
Additional Checks & Persistence
Being a rather regular sample of adware, Advanced Window Manager performs a series of system checks to determine system’s location. By checking the values of several registry keys, the malware obtains the networking information. It is unlikely that it has any sort of geofence, so this data is mainly needed to target the advertisements correctly.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\InterfaceSpecificParameters\
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient\DnsPolicyConfig
After that, the malicious program edits another set of registry keys related to Windows services and drivers. This is where it gains persistence by adding the values that will associate its files with some of the drivers/services in the system.
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MpKsl9a97d018\Parameters
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\MpKslcbc6775c\Parameters
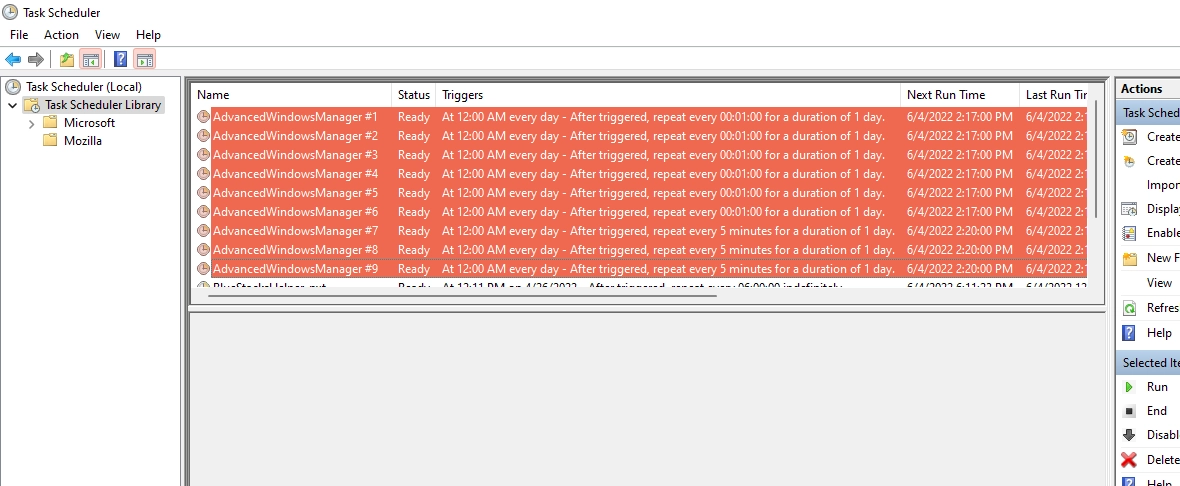
Advertising, Search Redirects and Browser Hijacking
After all the preparations, Advanced Window Manager starts acting as adware or browser hijacker. The most common scenario after installing this kind of software is browser hijacking. PUA changes the homepage and search engine to the one it advertises (usually Bing or Yahoo). It is also common to see a no-name engine like Chromstera as the homepage/search engine. In this case, all queries go through the above service, and the forced change of search engine is effective until the first restart of the browser.
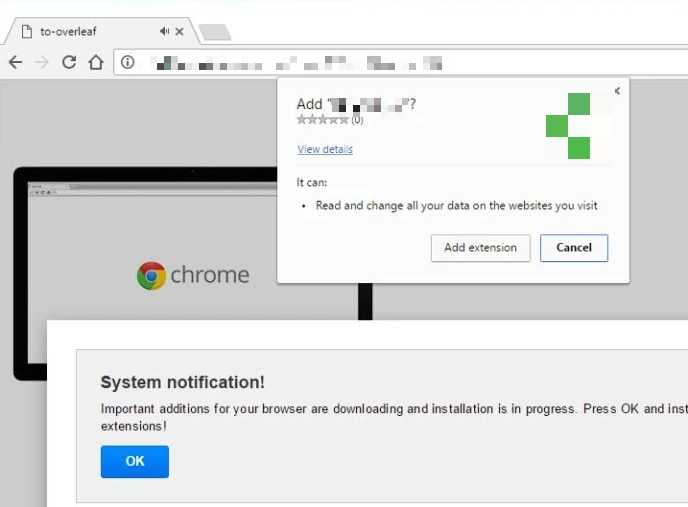
In addition to irrelevant search results, adware fills pages with ads and pop-ups, which makes it very difficult to use. The third aspect of a browser hijacker is collecting telemetry about the user. Although such software does not usually steal passwords or other sensitive information, it redirects all search queries through its server, thereby collecting general analytics about the user.
How To Remove Advanced Window Manager?
To remove Advanced Window Manager, you should use an advanced anti-malware tool. GridinSoft Anti-Malware is a great option. Run a Full scan, wait for it to finish, and follow the prompts.
You may also need to reset your web browsers. To do this, open the Tools tab and select Reset Browser Settings. In addition, I recommend that you enable the Internet security module, which protects against Internet threats. To do this, go to the Protect tab and activate the Internet Security checkbox.