Have you experienced an error popup which specifies on missing DLL files and pondered what really are DLL files? For what reason do we require them and what are the upsides of DLL files? They are dynamic libraries that can be called by applications amid run-time. They assume a noteworthy part in diminishing code delicacy and execution change.
In Windows-based PCs, all the time we run over DLL files that don’t enable some product to run. We get error messages disclosing to us that some specific DLL files are absent. To comprehend this issue, we scan for that specific file on the web and get the product working.
Understanding DLL: its working mechanisms and its importance for programs.
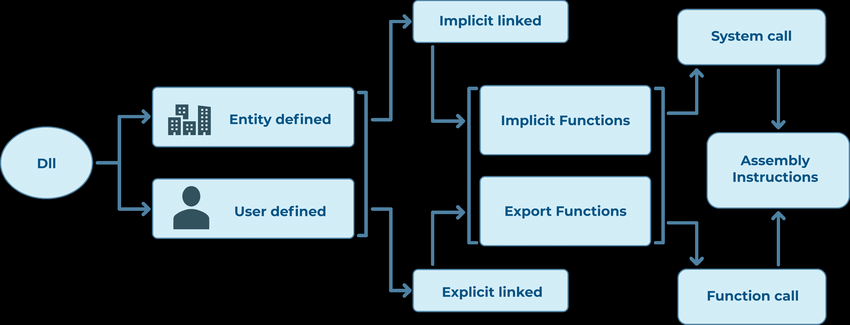
DLL stands for Dynamic-Link Library. It’s Microsoft’s usage of the common libraries. It’s a kind of file that has guidelines that different apps can call to do certain stuff. This enables distinctive programs to share a solitary file and make utilization of its capacities even all the while. Along these lines, a DLL file disposes of the requirement for numerous duplicates of a similar file. It contains classes, capacities, factors, UIs, and assets like symbols, pictures, files and so forth.1
On a wide range of working apps, you’ll experience two sorts of libraries — static libraries (.lib) and dynamic libraries (.dll). While static libraries are connected to executable files that gather time, the dynamic connected libraries aren’t connected until run-time. A dynamic library is a remain solitary record that can be separately refreshed without changing the EXE file itself.
How DLL document is utilized?
At the point when an EXE file runs, the Windows working framework locate the table of information connected to it, including the rundown of capacities from some DLL file. After this, the loader code searches for that specific DLL file and loads it. In that DLL file, there’s another rundown, named trade list, that associates each capacity of DLL files utilizing particular locations.
Advantages
- As said over, a DLL file diminishes the duplication of code that is put away on the circle. This enhances the execution of the program running in frontal area and foundation.
- It additionally helps in building huge measured applications that need loads of projects or dialect adaptations for secluded design.
- Another enormous favorable position of utilizing DLL files is that the establishment or change in DLL isn’t trailed by relinking it with the programs. In this way, a solitary fix will profit various programs in one go.
Disadvantages
- Introducing a solitary DLL file is frequently a swathe for a bigger issue.
- DLLs from DLL download websites are frequently obsolete and are not endorsed for DLL files.
- DLLs files from DLL download sources might be contaminated with viruses
- DLL download sites could have DLL files that can bargain your PC’s security
- Constant DLL errors: because of countless documents and their utilization recurrence, DLL-related errors are exceptionally normal. At whatever point we experience such mistake, our arrangement of activity is to look them on the web and set it back in its place.
- As a DLL file is regularly utilized by numerous programs, it’s stored in areas like C:\Windows\System32 and C:\Windows\SysWOW64. Such an allocation makes DLL files vulnerable for malware attacks2.
Be mindful online!
- More about DLL purpose : wikipedia.org/Dynamic-link library
- Usage of DLL vulnerabilities for massive cybercrime in October, 2020