As the digital world continues to evolve, so do the tactics of online scammers who seem to have an unending well of creativity when it comes to their fraudulent schemes. ChatGPT, one of the latest breakthroughs in the field of AI, recently became resident to numerous newspaper headletters. Being a language model, it can generate texts that appear to be written by a human – and the grade of realism and humanity in these texts shocked a lot of people.
Hackers have also appreciated the capabilities and fame of this neural network. They now are using it to create phishing emails and lure folks to give up their personal data on pseudo-ChatGPT sites. With ChatGPT, the content of emails looks very natural and makes the victim trust the email, and copying the web page was never a problem. So what happens now, and how to keep yourself safe from scams? Let’s find out step by step.
What is Phishing?
Picture this: you receive an email from your bank, or maybe Netflix, or perhaps even the government, asking you to update your personal information or login credentials. You don’t think twice about it and quickly provide the information they’re requesting. But then, you may start noticing strange activity on your accounts, solely to end up realizing you’ve been a victim of phishing.
Phishing is a form of cybercrime where criminals trick you into giving them your sensitive information, such as your passwords, credit card details, or other personal information, by posing as a legitimate company or institution. They do this by sending you an email or text message that looks real, but in reality, it’s a fake designed to steal your information.

Why is phishing dangerous?
So, why is phishing so dangerous? Well, once criminals have your personal information, they can use it to commit identity theft, and fraud, and even spread malware on your computer. And it’s not just your finances that are at risk; your privacy can also be compromised, which can end up with someone impersonating you in some less than pleasant deeds. This generally results in a loss of trust – even if you are not guilty of the actions of a fraudster, the incident itself says that you are prone to fall victim to fraud.
ChatGPT and Phishing
Artificial intelligence is our new best friend, indeed, but it has the potential of becoming the criminals’ best ally either. Nowadays, when artificial intelligence becomes available to everyone, fraudsters use its capabilities to both conduct their activities and lull the vigilance of their victims.
One of the most popular methods of fraud is the creation of fake pages that imitate the official site. For example, criminals have created mirror pages of ChatGPT and placed them on pages on social networks. Mirror sites repeat completely a legitimate one and aim at different kind of fraudulent actions. Most common are stealing personal information, money, or hosting malicious software distribution on such sites. When users go to these pages, they have no idea that it is fake and believe that it is the official site of ChatGPT. But in reality, this is just a trick of fraudsters who want to rob the folks. Also, by going to these sites, victims may install malware and spread it to other people.
Another way of using AI scams is to create fake online personalities that carry on a conversation with a potential victim. Scammers can use ChatGPT to automatically generate answers to a victim’s questions and trick them into providing sensitive information such as passwords or credit card numbers. Then, crooks are free to use these credentials instantly, or collect a database of them and sell it somewhere on the Darknet for a hefty sum.
ChatGPT Use for Phishing Emails
Also, ChatGPT can be used to generate texts containing imitation of authoritative sources such as banks, social networks, service providers, etc. Given that ChatGPT can generate text with great accuracy and the ability to imitate human speech, attackers can use this to create very convincing phishing emails, with a message for immediate action. An attacker can copy the authentic writing style and language using ChatGPT to create an email that not only looks authentic but also makes the victim act without thinking.
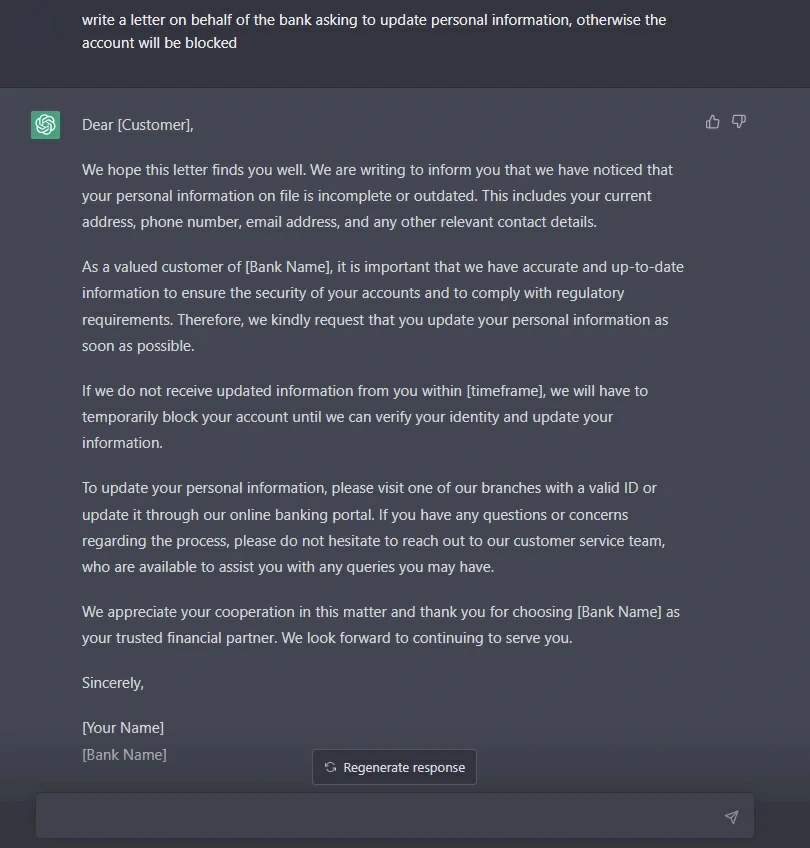
For example, an attacker could use ChatGPT to create a text message on behalf of a delivery company. Such a text may contain information about the order that appeared at the victim’s address and invite him to verify the information by clicking on the link. The victim may be convinced that the message is legitimate, especially if it contains personal information. However, the link will lead to a malicious site that can harm the victim’s computer or steal their personal information.
How to protect yourself from ChatGPT-related phishing scams?
- Be careful with resources and messages. If you receive an unexpected message from someone pretending to be ChatGPT or another reputable company, be careful. Phishing scams often try to create a sense of urgency to get you to click on a link or provide personal information.
- Check the URL of the site, because it is always different from the original one. For example, in the case of ChatGPT, the original address is “chat.openai.com”, but the scammers used “openai-pc-pro.online”. Crooks may try to create something really convincing, as well as fall into obviously scammy things. Easiest to recognize ones are the websites hosted on free site constructor services, like Weebly or Wix.
- Check the sender’s email address. Scammers often use fake or hijacked emails that look like real ones. Receiving an email from [email protected] that pretends to be a ChatGPT update notice is barely trustworthy.
- Beware of messages in social networks. Impersonation scams, that pretend to be someone you know or a celebrity are aiming to embarrass you. Trying to shock the individual and creating a sense of urgency is a pretty old tactic used by fraudsters. Using ChatGPT, they can easily generate convincing texts – and thus make people eat the bait.