At the RSA 2020 conference, ESET specialists spoke about the new Kr00k vulnerability (CVE-2019-15126) that can be used to intercept and decrypt Wi-Fi traffic (WPA2). Researchers believe that the Kr00k vulnerability in Wi-Fi-chips affects more than a billion devices.
This problem affects any device that uses the solutions of Cypress Semiconductor and Broadcom, from laptops and smartphones to routers and IoT devices. Experts tested and confirmed the problem for iPhone, iPad, Mac, Amazon Echo and Kindle, Google Nexus, Samsung Galaxy, Xiaomi Redmi, Raspberry Pi 3, as well as Asus and Huawei Wi-Fi routers. In total, the problem threatens about a billion different gadgets.
The essence of the Kr00k problem comes down to encryption, which is used to protect data packets transmitted via Wi-Fi.
“Typically, data packets are encrypted with a unique key, which depends on the Wi-Fi password set by the user. However, for Broadcom and Cypress chips, this key resets to zero if the process of dissociation, that is, a temporary shutdown, which usually occurs due to a bad signal. The Wi-Fi devices dissociate many times a day and then automatically reconnect to the previously used network”, — say ESET researchers.
According to ESET experts, attackers can provoke the transition of the device into a prolonged state of dissociation and receive Wi-Fi packets intended for it. Then, by exploiting the Kr00k bug, attackers can decrypt Wi-Fi traffic using a “zero” key.
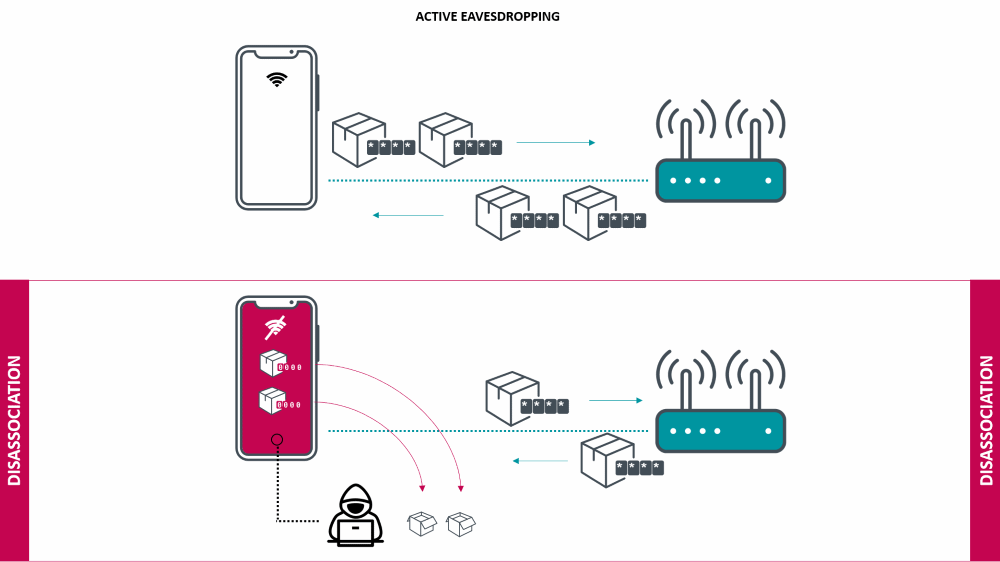
The Kr00k issue affects only Wi-Fi connections using WPA2-Personal and WPA2-Enterprise WiFi with AES-CCMP encryption. Therefore, the inclusion of the WPA3 protocol on the vulnerable device should protect against the attacks described by specialists. In addition, the vulnerability is unlikely to be useful to botnet operators for automated attacks, as it requires the attacker to be close to the victim (within the range of the Wi-Fi network).
Researchers notified manufacturers of the vulnerability two months ago, so by now many devices should have already received patches.
“Depending on the type of device, this may mean installing the latest OS or software updates (Android, Apple, and Windows devices; some IoT devices), but you may also need a firmware update (access points, routers, and some IoT devices)”, – say the experts.
Experts note that the Kr00k problem is in many ways similar to the sensational KRACK vulnerability, discovered in 2017 and forcing manufacturers to hurry up with the transition to WPA3, as well as the DragonBlood problem, which already posed a threat to WPA3. Additionally, security experts recall that recently discovered that the Emotet Trojan, which became the most dangerous threat of 2019, spreads through accessible Wi-Fi networks.
At the same time, it is emphasized that Kr00k is in many ways different from the listed threats and it will be easier to fix the consequences in this case.