The Department of Homeland Security (DHS CISA) Cybersecurity and Infrastructure Protection Agency (DHS CISA) has published security guidelines for the private sector and government agencies. CISA said that Chinese hackers associated with the Ministry of State Security of the Republic of China are attacking organizations in the United States and exploit bugs in F5, Citrix, Pulse Secure and Microsoft Exchange.
According to CISA experts, over the past year, Chinese hackers have regularly scanned US government networks in search of network devices, and then used against them exploits for resh vulnerabilities, trying to gain a foothold in vulnerable networks and continue lateral movement.
The Cybersecurity and Infrastructure Security Agency (CISA) has consistently observed Chinese Ministry of State Security (MSS)-affiliated cyber threat actors using publicly available information sources and common, well-known tactics, techniques, and procedures (TTPs) to target U.S. Government agencies”, — says CISA report.
According to the report, some of these attacks were successful, and the attackers achieved their goal.
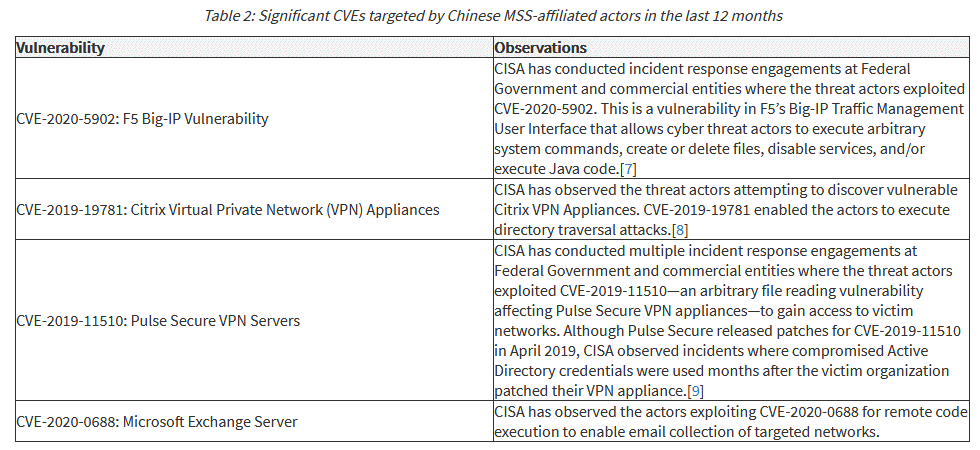
The main targets of the Chinese hackers were F5 Big-IP load balancers, Citrix and Pulse Secure VPN devices, and Microsoft Exchange mail servers. Serious vulnerabilities have been identified in all of these products over the past year, including: CVE-2020-5902, CVE-2019-19781, CVE-2019-11510, and CVE-2020-0688.
Having infiltrated the network, Chinese hackers seek to advance further and steal data. For this is used a variety of tools (including open source and legitimate), the most common of which are the Cobalt Strike platform, as well as the China Chopper Web Shell and Mimikatz tools.
ZDNet journalists note that not only Chinese cybercriminals are interested in the listed above vulnerabilities.
“In addition, Chinese hackers aren’t the only ones targeting these particular networking appliances. The devices listed above have also been targeted by Iranian state actors, according to a report from the private cyber-security sector and a cyber-security alert published by the FBI last month”, — report ZDNet journalists.
Let me remind you that recently specialists of the Crowdstrike and Dragos companies noticed that the Iranian “government” hackers are putting on sale access to the networks of compromised companies, and provide access to other criminal groups.
I will also remind you that the US authorities warned of a possible intensification of attacks by Iranian hacker groups on the public sector. Perhaps their warning was reasonable.