Sync.clearnview.com is a website that users can see in a number of alerts from antivirus programs. Simultaneously, it may appear during the normal browsing activity, and display unwanted and unpredicted results. Its presence in any form is a marker of malicious activity, and in this article, I will explain how to remove it and prevent its appearance in future.
What is sync.clearnview.com?
In its very essence, sync.clearnview.com is a website that acts as one of the endpoints in malicious web browser redirection campaigns. Con actors use computers infected with a specific malware, known as browser hijacker, to route user requests through a sequence of landing pages. Each of them collects information about the user, which is further sold to data brokers and other malicious actors.
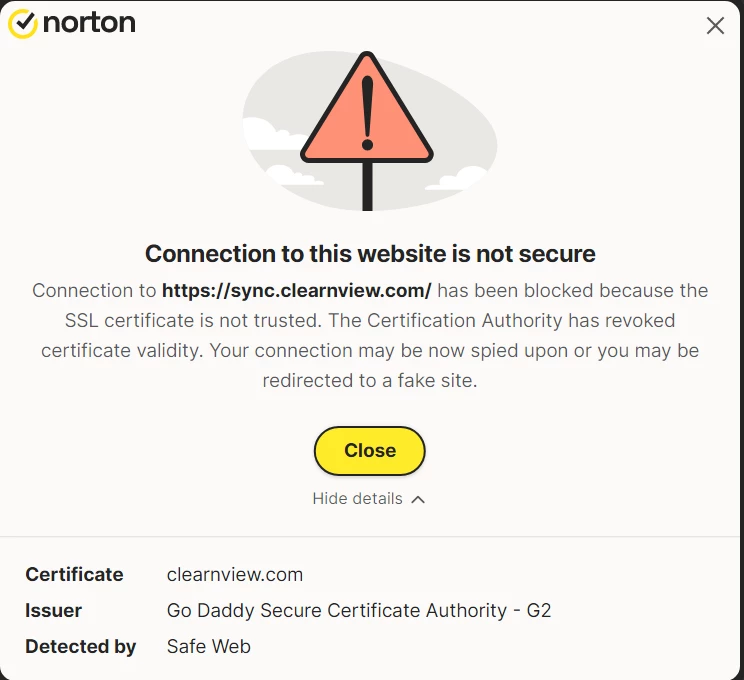
Users started to complain massively about their antiviruses going crazy with alerts about preventing the connections to sync.clearnview.com and similar sites. Two particular ones are Norton and Bitdefender, but it is highly possible that others detect this page, too.
URLs associated with Clearnview virus
The root web page does not contain anything, and returns an error shall one try opening it in the web browser. Real connection happens only when the browser hijacker tries to re-route the user request. In this case, the malware generates a query that contacts a specific URL, so all the malicious magic happens without any problems.
At that exact moment, antivirus software starts detecting this unusual traffic and shows the “sync.clearnview.com connection stopped”. Security programs know that the site is dodgy, thus block the connection at the very beginning. Nonetheless, it is not enough: the source virus remains active, so the redirection attempts will continue, and so will alerts from the antiviruses.
Aside from the constant notifications from the antivirus software, one may notice anomalous behavior of the web browser when the hijacker virus is active. But all of it eventually concentrates around collecting user information and forcing them to visit questionable websites. This, in fact, is a major risk, as it is quite common to see phishing pages and scams among ones promoted by browser viruses.
How did I get infected?
Browser hijackers are pretty common to find in questionable software and on websites with pirated content. The latter often open additional tabs to every click on their content; those tabs ask the user to install “useful browser extensions” to keep browsing the content. As you may know, none of these extensions grant you access to the content, and most often just carry malicious code.
Pirated software is a different propagation scheme, yet it concentrates on the very same approach with browser extensions. The latter has become an exceptionally popular vector for spreading viruses, consider checking out our dedicated article regarding browser extension security.
How to Stop Sync.clearnview.com?
Unstopping notifications about the blocked connection mean that your current antivirus is not able to delete the source malware. This is where GridinSoft Anti-Malware comes in handy: its multi-component detection system will quickly detect and remove the intruder, stopping any further troubles with your web browser. Download it by clicking the banner below and run a Full scan, to check the most remote parts of your system.
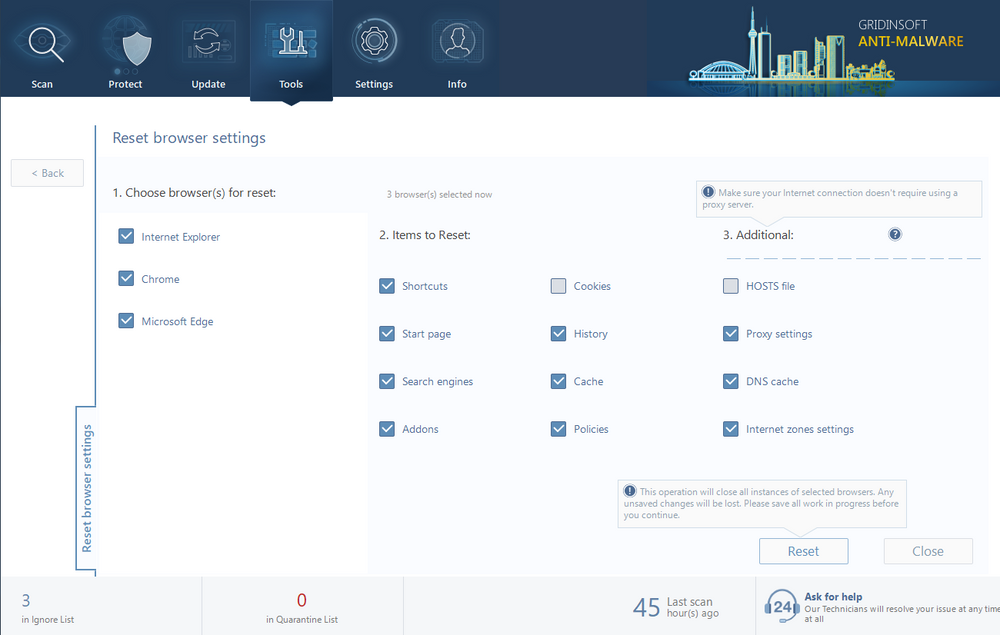
After the scan, I will recommend you to reset your browser. Malware often does a lot of changes to configuration files, and they remain in place even after the virus removal process. You can reset each browser individually, or use GridinSoft Anti-Malware for that purpose.
In GridinSoft Anti-Malware, open Tools Tab → Reset Browser Settings, and in here, opt in for the web browsers you need to get back to the original state. After that, click the Reset button and wait for a few seconds to get your web browser as good as new.