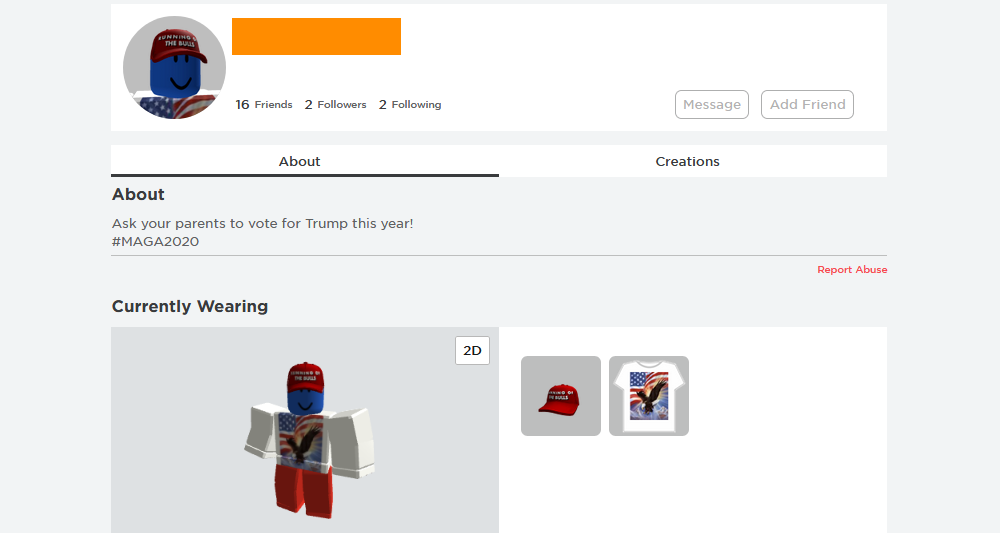
According to the ZDNet publication, unknown attackers hack Roblox accounts and leave a message “Ask your parents to vote for Trump this year! #MAGA2020 ” in about 1800 users’ profiles on Roblox.com.
Judging by the complaints of the victims, which can be found on Reddit, on Twitter and so on, the first attacks began last week.
“But the matter did not stop with a text message in support of Trump: the avatars of the hacked accounts were also changed and now show clothes typical of Donald Trump’s supporters: a red cap and a T-shirt with an American flag and a bald eagle”, – say ZDNet reporters.
Many victims who reported hacking their accounts on Roblox forums admitted that they reused the same passwords or had very simple credentials, unstable even before a simple brute force attack.
Many also admit that they did not include two-factor authentication. Roblox uses a 2FA email-based system, it requires the user to first enter a username and password, and then a one-time code that is sent to the email specified by him.
Currently, it is unclear how hackers managed to compromise such a number of accounts, and Roblox representatives did not comment on the situation. However, KE-LA information security experts told ZDNet that they were able to find Roblox user names with plaintext passwords on paste sites. Journalists checked dozens of users from these lists and found that many of them really called to vote for Trump. Their publication suggests that this is how most accounts were hacked.
At the same time, attacks are still ongoing.
“When the researchers first began to study the problem last weekend, they counted about 750 hacked profiles. During the week, their number remained almost unchanged, stopping at around 1,000 hacked accounts, but now the number of compromised accounts is growing again. So, in just an hour, hackers increased the number of hacks from 1680 to 1820”, – reported in ZDNet.
Since there are a lot of children among Roblox users, experts recommend their parents to help their children to choose more secure passwords and enable 2FA.
Let me remind you that researcher found that every 142nd password is “123456”.