Huge number of fake Robux generators recently appeared on a range of websites with .gov, .mil, and edu. They commonly pose as PDF files, enriched with keywords that boost their SEO ranking to show up on top of Google search results. By parasiting on legit domains of government, military, and educational organizations, they also avoid detection from network filters.
Fake Robux Generators Flood Legit Websites
On April 9, 2024 researchers from VX-Underground (VXUG) shared a surprising discovery on their X (Twitter) page. Government sites, particularly ones hosted on .gov, .mil, and .edu domains, are flooded with PDF documents that offer to download Robux generators. Robux is a virtual currency in the Roblox game that is particularly popular among teenagers. Normally, players should purchase or earn it, but it is always tempting to cheat and gain a lot in a few clicks.
At the moment, a Google search query with a dork to display only a specific domain with the keyword “Robux” returns what you can see below. Interestingly enough, .edu domains affected by this spam are already cleaned. This probably happened because VXUG reported them first.
The contents of the said PDF files are pretty much the same. Despite having different designs, all of them have one or several links/buttons that offer to download the content. The vast majority of these sites lead to the ashnews[.]info/flika website. To fill up the rest, the authors of this mess added a completely senseless text with hundreds of keywords related to Roblox and Robux.
Such tactic is known as SEO poisoning and aims at a short-term, yet rapid push to the top of Google search results. Search engines detect and remove pages that practice such a trick rather quickly. Still, they managed to gain a considerable amount of traffic at this point.
How Dangerous are Fake Robux Scams?
Same as any other way to hack a game, Robux generators are not safe – there is always a high chance of getting malware inside or instead of one. The latter is true in the case of Robux generators spread on the government and military sites. Links or buttons in the document can lead to malware downloading, as well as throw the victims to a fake tech support page.
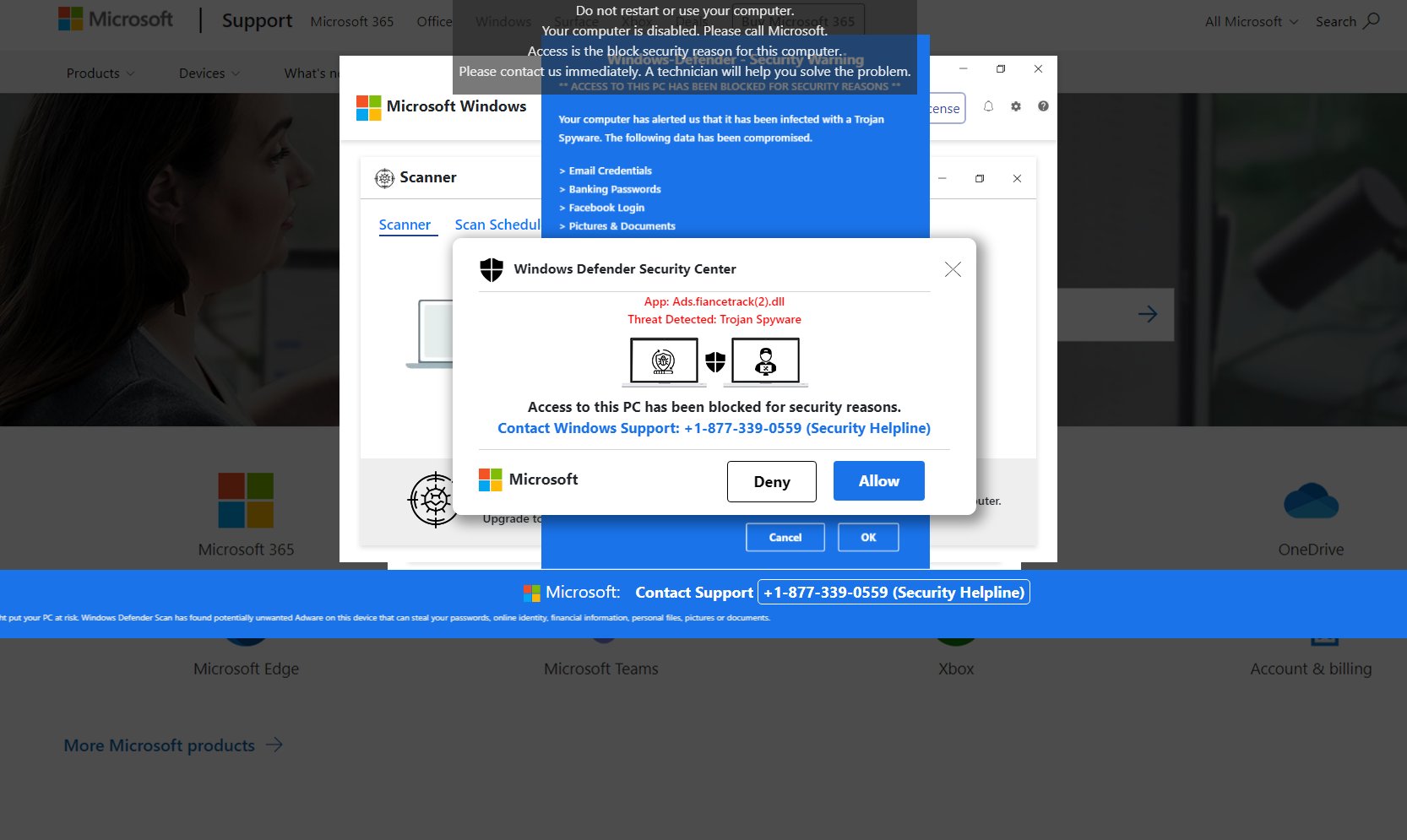
While looking way too obvious for being effective, this scam obviously targets the main audience of the Roblox game – guys in their early teens. You will barely find a tech-savvy person among them, let alone the one who can distinguish a scam by the looks of it. This explains the clumsiness of the campaign – there’s no need to make it any better.
How to Protect Yourself?
The very first advice in protecting against such scams is to remember that there’s no such a thing as free. Whenever someone offers you to get something without any pay, they most likely suppose that you’d pay for it in another way, sooner or later. At the same time, online scams evolve continuously, making themselves harder to spot.
To get the protection against online scams, I recommend using GridinSoft Anti-Malware. Its network scanner will protect you from scam websites, and will also repel malware that manages to get into the system. Its multi-component detection system is effective even against the most modern and evasive threats – consider trying it out.