VirusTotal specialists presented a large report on the recent ransomware activity and said that almost 95% of ransomware targets Windows. To do this, experts analyzed 80 million samples of ransomware.
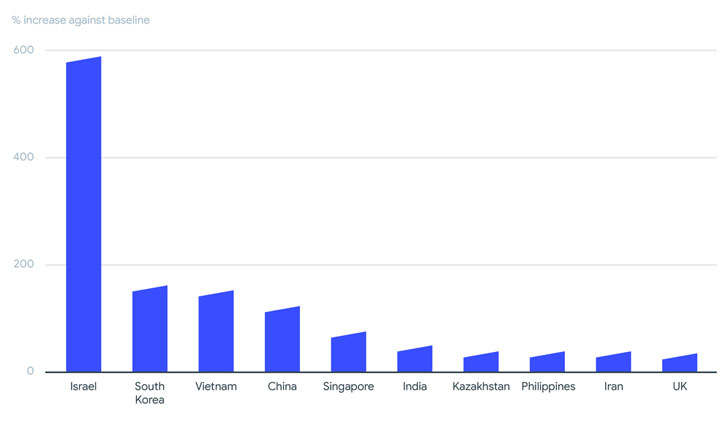
It turned out that in 2020 and the first half of 2021, a total of 130 different ransomware families were detected, and Israel, South Korea, Vietnam, China, Singapore, India, Kazakhstan, the Philippines, Iran and the United Kingdom are most affected by their attacks. At the same time, it is noted that such high numbers for Israel are most likely due to the fact that many companies there automate their applications.
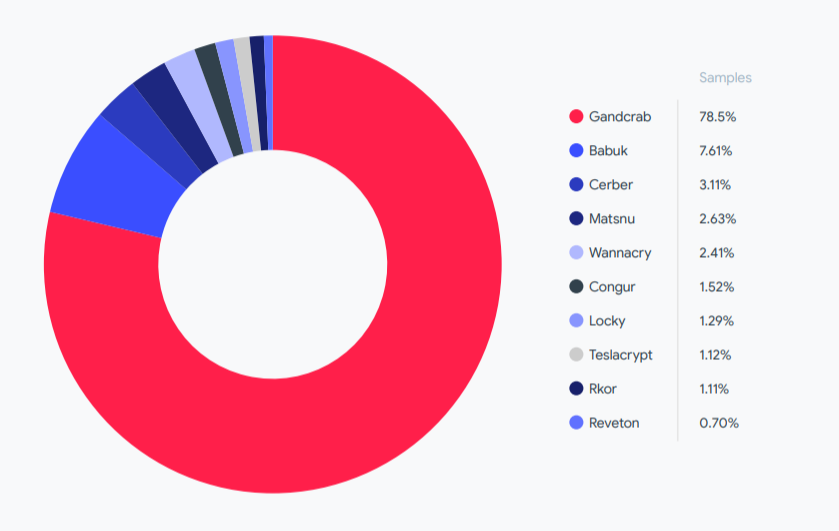
The researchers write that most of this activity came from the GandCrab (78.5%) hack group, followed by Babuk (7.61%), Cerber (3.11%), Matsnu (2.63%), Wannacry ( 2.41%), Congur (1.52%), Locky (1.29%), Teslacrypt (1.12%), Rkor (1.11%) and Reveon (0.70%).
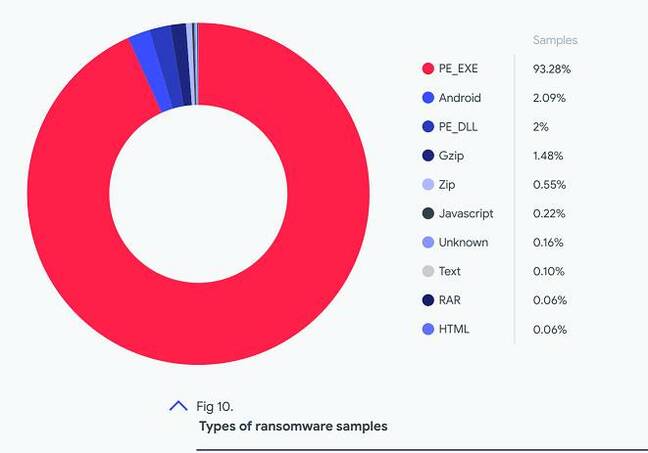
The report states that 93.28% of the ransomware detected are executable files for Windows operating systems, and another 2% are Windows DLL files. Android accounts for only 2% of files, and in mid-2020, several EvilQuest malware samples were detected targeting Mac.
The study also emphasizes that only 5% of analyzed malware samples were associated with various exploits (usually, we are talking about privilege escalation in Windows, SMB information disclosure and remote code execution).
Let me remind you that I also said that Microsoft estimated that ransomware attacks take less than 45 minutes.