A new Android backdoor, dubbed Xamalicious, was discovered by the researchers at the edge of 2023. This malware exhibits potent capabilities to perform malicious actions on infected devices. Malware reportedly exploits Android’s accessibility permissions to gain access to various sources of user data.
What is Xamalicious Malware?
As I’ve said in the introduction, Xamalicious is a backdoor malware designed for Android. It is based on a Xamarin framework, which eventually granted it the name, and some of the abilities. Typically for sophisticated examples of Android malware, it abuses accessbility permissions to gain access to things like clipboard, autofill forms, notifications, messages, and others.
Xamalicious operates in two stages. Initially, it gathers device metadata and contacts a command-and-control (C2) server. This first contact is crucial for determining further steps, as upon sending the initial data, malware masters should decide their further steps. If needed, the malware can deliver other payloads and run them as an assembly DLL at runtime. This enables complete control over the device, potentially leading to fraudulent actions such as ad clicks and unauthorized app installations.
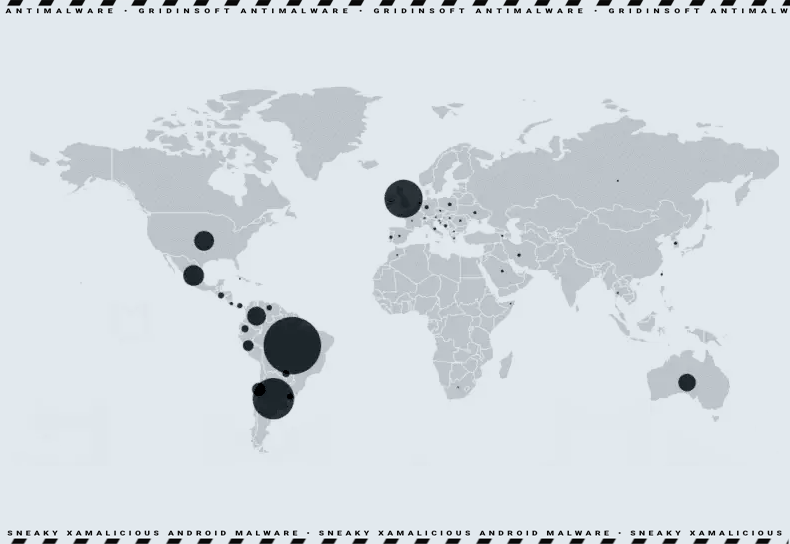
Researchers say about locating the threat within 25, some of which were even distributed through the official Google Play Store since mid-2020. Alarmingly, these apps have been installed at least 327,000 times, affecting users from Western Europe, South and North America and Australia.
Here some of these malicious apps:
- Track Your Sleep (com.shvetsStudio.trackYourSleep)
- Count Easy Calorie Calculator (com.lakhinstudio.counteasycaloriecalculator)
- Sound Volume Extender (com.muranogames.easyworkoutsathome)
- 3D Skin Editor for PE Minecraft (com.littleray.skineditorforpeminecraft)
- Logo Maker Pro (com.vyblystudio.dotslinkpuzzles)
- Auto Click Repeater (com.autoclickrepeater.free)
- LetterLink (com.regaliusgames.llinkgame)
- Essential Horoscope for Android (com.anomenforyou.essentialhoroscope)
Geography of Activity: Xamalicious Malware
Technical aspects
To evade detection, Xamalicious authors have encrypted all communications and data transmissions between the C2 and infected devices. The encryption is not limited to HTTPS protection but extends to JSON Web Encryption tokens. Such tokens use advanced algorithms like RSA-OAEP with 128CBC-HS256. This makes the malware difficult to analyze and detect.
Moreover, the first-stage dropper contains self-update functions for the main Android package file (APK), suggesting that it can be weaponized as spyware or a banking trojan without user interaction.
How to Protect Against Xamalicious Backdoor?
Xamalicious is not a ground-breaking malware sample, but its dangers should not be underestimated. The fact that it exploits the same Android features is not about its technological obsolescence. “Don’t change what’s working” – hackers stick to this rule, and it works out rather well.
To avoid the infection, exercise caution when downloading apps, especially from unofficial sources. Even more attention should be paid to the permissions you give to the programs. And, to seal the deal, consider running an anti-malware scan on your smartphone, at least once a week. This will ensure your data security.