Analysts at Digital Shadows have estimated that there are currently more than 15 billion stolen logins and passwords, including more than 5 billion unique credentials, on the black market (hacker forums, underground marketplaces, paste sites, file sharing, and so on).
For more than a year, the company has been collecting data from the abovementioned sources, and researchers note that most of these usernames and passwords are offered and published free of charge, and the actual amount of compromised credentials should be even higher.
Let me remind you, by the way, that users seldom change passwords even after data leaks.
“The fact is that nowadays attacks, aiming account hijacking are simple and cheap as never before, and many specialized hacker tools can be bought for about $4″, – write Digital Shadows researchers.
If we talk about the cost of credentials, the average price of one account on trading floors on the darknet and the Internet is $15.43. Moreover, the data of many compromised accounts can be found in various sources, and the information will be relevant, which suggests that their owners do not even suspect a hack.
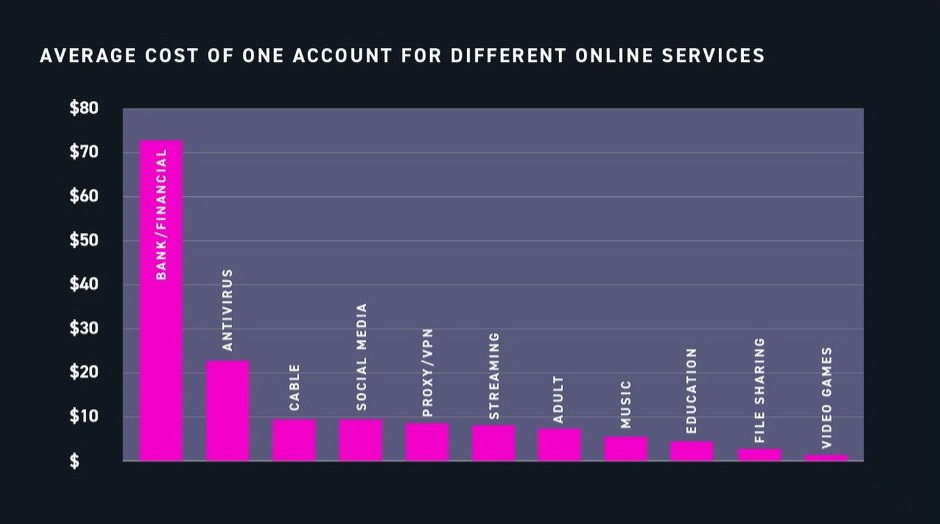
The most expensive ones are predictably related to banking and other financial accounts: their average price is approximately $71, although some of these accounts can be priced at $500 or more.
Interestingly, anti-virus accounts cost a little over $20, while other types of accounts most often sold for less than $10 (including social networks, VPN, streaming, education, music, file sharing, video games and adult content).
“The same principle works here, and explains why stolen accounts of streaming services sell well on the black market: many buyers just do not want to pay the full price for an antivirus subscription”, – explain the researchers.
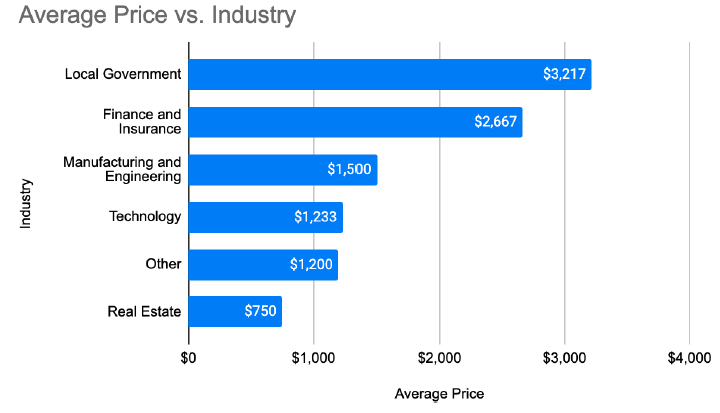
Also often on the black market you can come across assumptions about the sale of access to critical systems of companies and organizations. So, access with domain administrator privileges can cost about $120,000, with an average price of just over $3,100. Pricing in this case depends on the particular attacked industry, in particular, municipal authorities and the financial sector are usually the most expensive.
Digital Shadows notes that accounting usernames are also in high demand, especially accounts containing words such as “invoice”.