Last weekend, unknown hackers managed to break into the mail server of the Federal Bureau of Investigation (FBI). Hackers used the access to send letters that imitated FBI alerts about cyberattacks and data theft.
Spamhaus, a non-profit spam-tracking organization, reported that such emails were delivered to tens of thousands of recipients in two waves. At the same time, experts believe that about 100,000 letters are only a small part of the campaign.
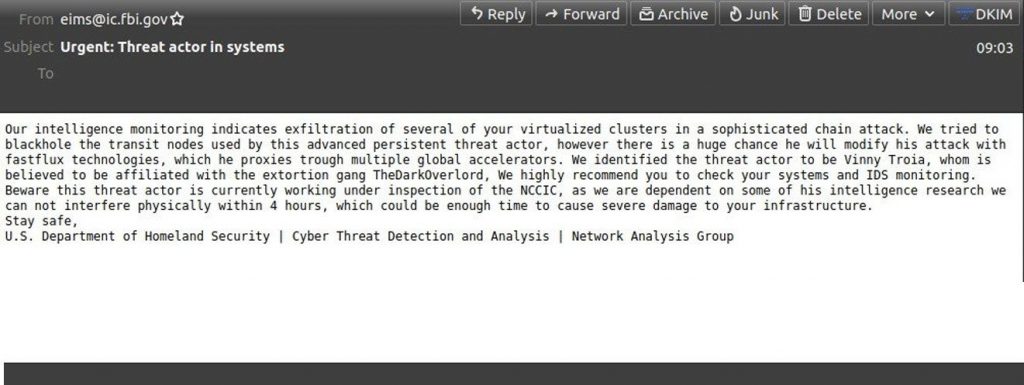
According to Spamhaus, messages came from a legitimate address [email protected], with IP 153.31.119.142 (mx-east-ic.fbi.gov), and the subject line said “Urgent: Threat actor in systems”.
Spamhaus said the mailing was followed by a rash of phone calls and letters from concerned organizations seeking more information on the attacks on FBI offices. Although the letters were clearly fake (they contained many spelling errors), the newsletter caused serious panic, as the letters passed the SPF and DKIM security checks, that is, they were sent from real FBI servers and bypassed all spam filters.
Worse, messages from the attackers reported that a certain Vinny Troia was responsible for these attacks. Troy is a renowned cybersecurity researcher who leads darknet research at NightLion Security and Shadowbyte. The fact that the attackers blamed Vinnie Troy for non-existent attacks was well commented on by renowned information security specialist Markus Hutchins.
Troia himself writes on Twitter that, in his opinion, the accident is the work of a man known as pompomourin. In the past, this person has already been involved in incidents aimed at damaging the investigator’s reputation.
Moreover, a few hours before the attack on the FBI mail server and the sending of spam, pompompurin contacted the researcher on Twitter and advised him to “enjoy” what was about to happen.
The FBI has already confirmed the break-in. The agency said it was already investigating the incident, and the compromised server was temporarily shut down to stop spamming.
Apparently, the hackers took advantage of a vulnerability in the software running on the server to send messages. At the same time, the compromised machine was isolated from the agency’s corporate mail and did not give access to any data or personal information on the FBI network.
Well-known cybersecurity journalist Brian Krebs notes that the LEEP (Law Enforcement Enterprise Portal) allowed anyone to apply for an account, but the registration process required filling out contact information.
As a result, using a special script, the attackers were able to change the parameters, specify the subject and text of the email of their choice, and automate the sending of messages.
Let me remind you that I also wrote that List of suspects in terrorism that are monitored by the FBI leaked to the network.