Android:TrojanSMS-PA is a detection name from a built-in Huawei security tool. This particular name recently appeared as a detection of the Google app on Huawei devices. However, this name is not a 100% false positive, and here is why.
What is Android:TrojanSMS-PA?
As I said, Android:TrojanSMS-PA detection name is one of hundreds used by an antivirus tool that is built into the Huawei smartphones and tablets. Since the company ships the devices with their own builds of Android, that lack Google apps, you may have used this antivirus without even knowing. And there, actually, can be the reason for such a detection.
Back in 2020, Huawei was prohibited from using Google apps on their smartphones. With time, the co created their own ecosystem of apps, and apps developed by Google are now obviously treated as third-party. According to user reports, the Android:TrojanSMS-PA detection name often points at the Google app itself.
Is Android:TrojanSMS-PA false positive?
Most probably, the Android:TrojanSMS-PA detection is a false positive. Such things happen to pretty much any antivirus program – a mistake of the heuristic system or issues with certificate recognition. The chance that Huawei would make their antivirus to intentionally detect the Google app is miserable, especially since it will cause a storm of detections on user devices.
However, there is always a chance that the Android:TrojanSMS-PA detection is a real virus active in your smartphone. Most common malware samples for mobile devices include spyware, stealers, adware and fleeceware. To clear this up, you can investigate the detection yourself, or scan your device with a different mobile antivirus software.
What should I do?
First and foremost, don’t panic. Malware for smartphones is mischievous yet non-destructive. You are not likely to see your files encrypted, deleted, or bad things like that. Still, having your personal data stolen is nothing good either. That being said, let’s see how to understand whether the Android:TrojanSMS-PA is malicious, or just a false detection.
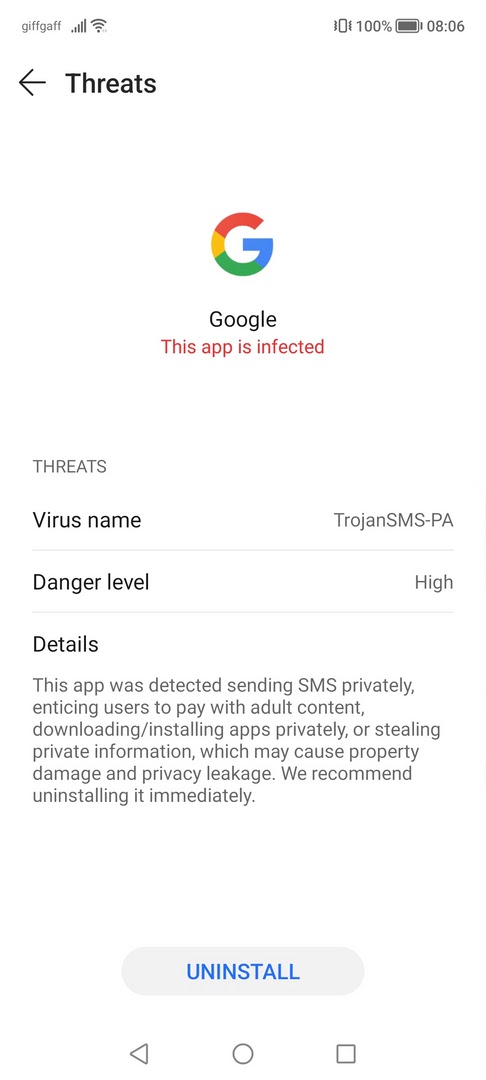
Once you see this detection, go to the Security app, and check what app it detects as TrojanSMS-PA. If it is a Google app – well, that is definitely a false positive. People already discuss the situation on various forums, and the only thing you need is ignore it and wait for a fix.
But when you see a strange file, or an app from a third-party source detected as TrojanSMS-PA, that’s the time to stay on the alarm. As I said, this detection is not 100% false positive, and in this configuration it may be a sign of a serious malware running in your system. I recommend using Trojan Scanner – a free and effective antivirus program, that will clear up the security situation on your smartphone.
I could not find Trojan Scanner on the app store. Thank you for the article.