Attackers are using a fake SafeChat Android app to attack users in the South Asian region. The malware is designed to steal call logs, text messages, and GPS locations from targeted smartphones. India’s APT group “Bahamut” is probably behind all this mess.
Bahamut Group Exploit Phony Android Application
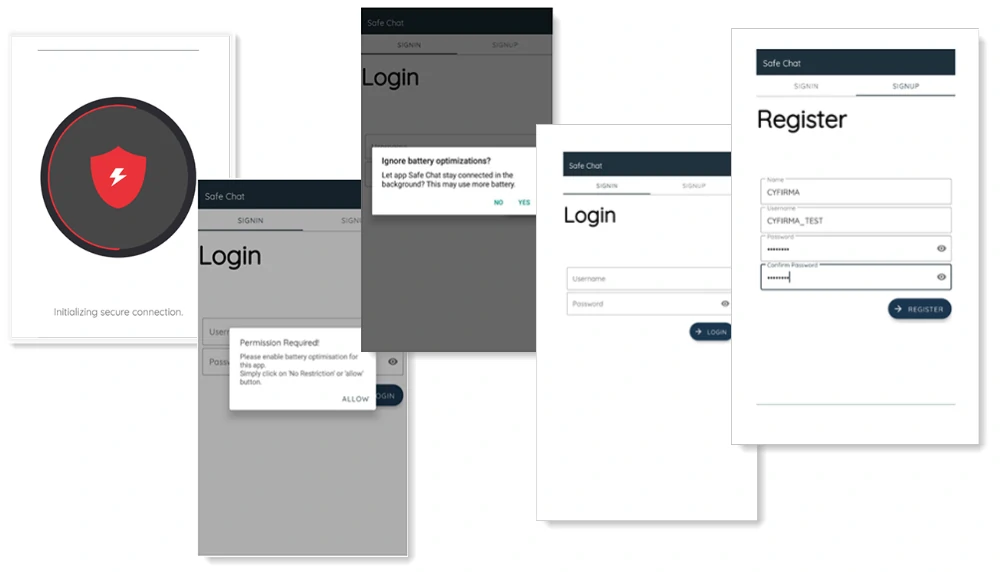
Recently, analysts came over advanced Android malware that targets individuals in the South Asia region. The malware is disguised as a chatting app known as “SafeChat,” which victims get via WhatsApp. Attackers use social engineering and often lure victims to install a chat app under the pretext of switching to a more secure platform. The app’s interface is typical for all messengers, which is not hard to copy from elsewhere. And that is why it effectively deceives users into thinking it is legitimate and safe. However, it allows the TA to extract all necessary information. The malware exploits Android Libraries to extract and transmit data to a command-and-control server.
It is worth noting that this SafeChat has nothing to do with a legitimate program of the same name. However, Bahamut APT does not try to mimic the one. Most probably, they picked a name exclusively for a clickbait, making no reference to the app’s legitimacy. Though, the original app is not recognized well enough to make its name work as a disguise.
State-Sponsored Activity
According to technical analysis, the Android spyware appears to be a variation of the well-known Coverlm malware. It is notorious for extracting data from popular communication apps such as Telegram, Signal, WhatsApp, Viber, and Facebook Messenger. Indian APT Bahamut group is behind the attack. In addition, the malware exhibits similar tactics used by the notorious APT group, DoNot, but with more permissions. Additionally, based on substantial evidence, experts have linked Bahamut to acting on behalf of a particular state government in India. Sharing the same certificate authority as the DoNot APT group and similar data theft methodologies, a common area of operation, and using Android apps to infect targets suggests close cooperation or overlap between the two groups.
“Safe Chat” Details
As I mentioned above, the Safe Chat app has a misleading interface that gives the impression of a genuine chat application. When first launched, it further manipulates victims by walking them through a seemingly legitimate user registration process, boosting their credibility and serving as a cover for embedded spyware. One of the most essential steps in the infection is the acquisition of permissions to use the Accessibility Services. The app used it to grant additional – and crucial – permissions to the spyware automatically. Having access to Accessbility Services allows the spyware to access the victim’s contact list, SMS, call logs, and external device storage and get accurate GPS location data from the infected device.
Safety tips
Although cyber-attacks are not new, it is always wise to be cautious of such incidents and take measures to ensure your safety. The following are some suggestions to safeguard yourself against SafeChat and other types of malware and maintain your Android device’s security:
- Install Apps from Trusted Sources. For your safety, we recommend that you only download and install apps from official places such as Google Play Store. Please avoid installing apps from unknown sources, which may contain harmful malware.
- Check App Permissions. It’s essential to be careful when downloading apps that request unnecessary permissions. If an app asks for access to sensitive data or unnecessary features for regular use, think twice before installing it.
- Keep Your Device Updated. It is essential to regularly update your Android device with the latest software and security patches. Manufacturers release these updates to fix any vulnerabilities and make your device more secure.
- Use Security Apps. Installing a trustworthy antivirus or security application from a reliable source is recommended to conduct regular scans on your device for potential threats and malware.