Sophos experts have discovered the Epsilon Red ransomware that exploits vulnerabilities in Microsoft Exchange servers to attack other machines on the network.
Experts write that the malware is based on many different scripts, and Epsilon Red operators use a commercial remote access utility in attacks.
Epsilon Red was discovered last week while investigating an attack on an unnamed US hospitality company. Attackers entered the corporate network using vulnerabilities in the local Microsoft Exchange server. The talk is about, of course, about the sensational ProxyLogon problems discovered in early 2021.
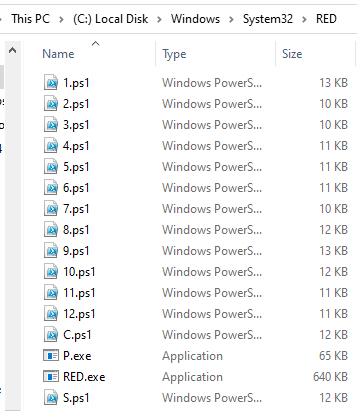
It is reported that Epsilon Red is written in the Golang (Go) language, and the launch of the malware itself precedes the work of a whole set of PowerShell scripts that set the stage for encryption. Most of the scripts are numbered from 1 to 12, but there are several that are named with the same letter. One of them, c.ps1, appears to be a clone of the Copy-VSS pentester tool.
Scripts have specific purposes:
- eliminate the processes and services of security mechanisms, databases, backup programs, Office applications, mail clients;
- remove shadow copies;
- steal the Security Account Manager (SAM) file containing password hashes;
- delete Windows event logs;
- disable Windows Defender;
- suspend processes;
- remove security products (Sophos, Trend Micro, Cylance, MalwareBytes, Sentinel One, Vipre, Webroot);
extend privileges in the system.
Once on the network, hackers reach other machines using RDP and Windows Management Instrumentation (WMI), and then install software and PowerShell scripts on them, which ultimately leads to the launch of the Epsilon Red executable.
Analysts point out that attackers are installing a copy of Remote Utilities, a commercial remote desktop tool, and the Tor browser on compromised machines. This is done to maintain a stable presence in the system.
The Epsilon Red attack can provoke real chaos in the company, since the ransomware has no restrictions on encrypting certain types of files and folders. The malware encrypts any files by adding the .epsilonred extension to them, and makes no exceptions even for executable files and DLLs, which can disrupt the operation of important programs and the OS itself.
The malware generally uses the godirwalk open source library to browse the directory tree.
In this way, Epsilon Red scans the hard drive and adds directory paths to the list of destinations for child processes that encrypt subfolders individually. As a result, many copies of the ransomware process are launched on the infected machines.
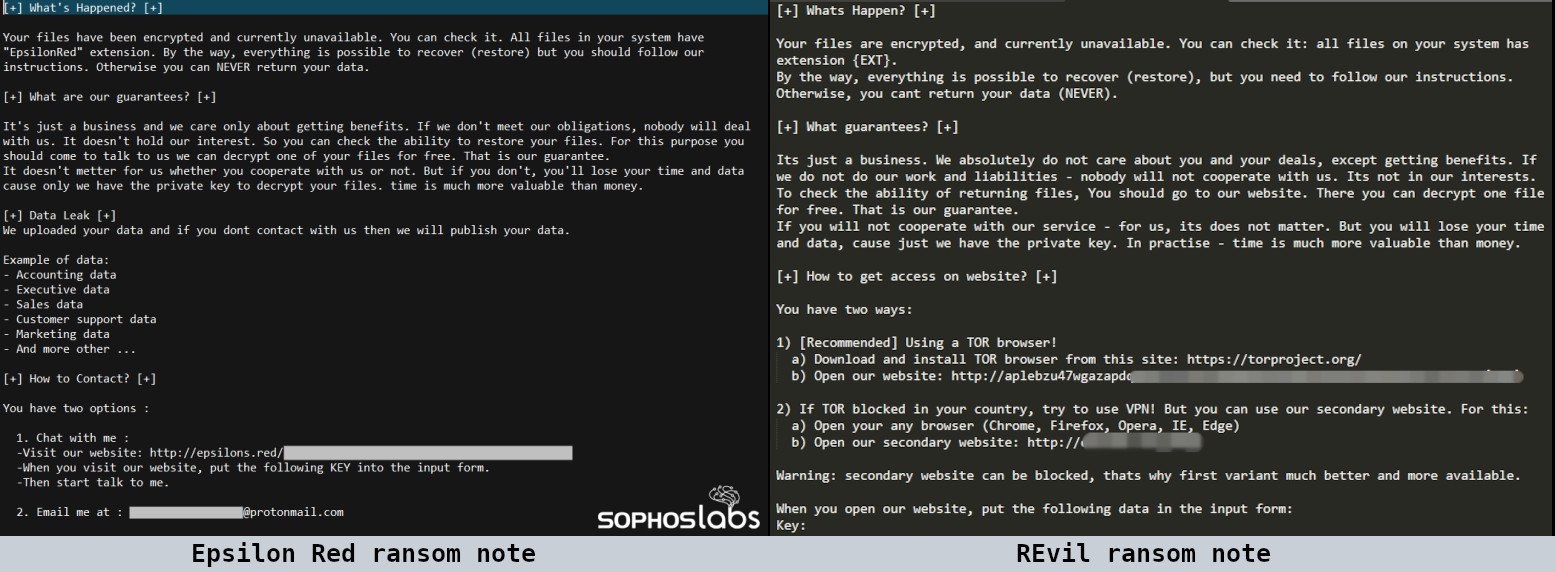
The ransom note is an updated version of the ransom note used by the ransomware REvil. However, the authors of Epsilon Red have tried to correct grammatical and spelling errors in the text.
According to Sophos, at least one victim of the ransomware has already paid the attackers a ransom of 4.28 BTC (about $210,000).
Although experts have not yet written anything about the attribution of malware, it is worth noting that Epsilon Red is a character in the Marvel Universe, a Russian super-soldier with tentacles who can breathe in space.
Let me remind you that I also wrote that Prometei botnet attacks vulnerable Microsoft Exchange servers.