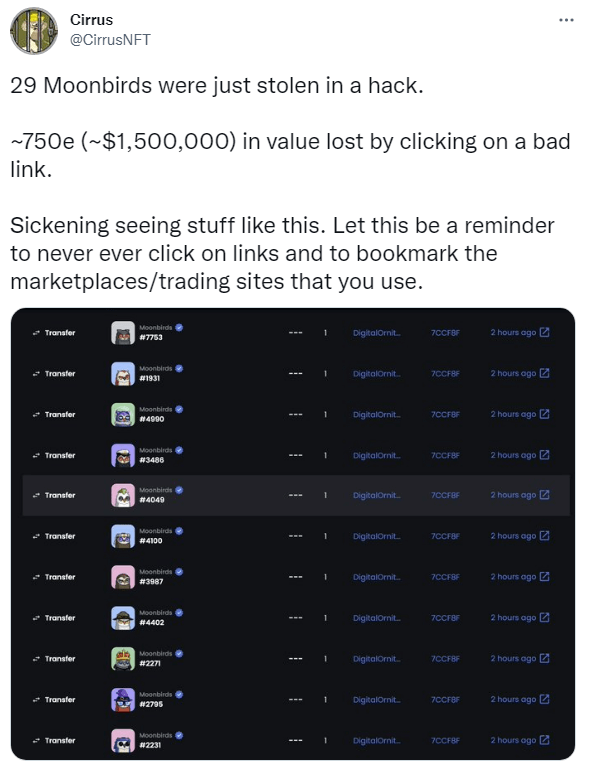
29 Moonbirds, NFTs amounting to around 750 ETC (approximately $1,5M) in value, were stolen from an unmentioned Proof Collective member as a result of a scam, according to the May 25 tweet by @CirrusNFT. The theft happened as the victim clicked an unchecked link signing a transaction offered by a scammer who pretended to be a law-abiding buyer.
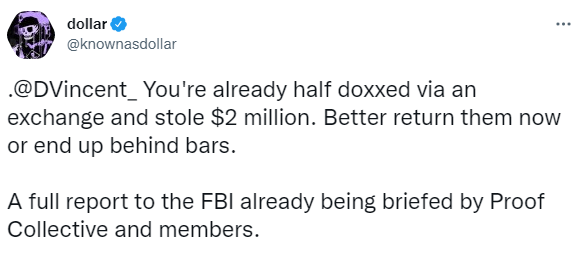
Another Proof Collective member, nicknamed Dollar (@knownasdollar on Twitter,) hinted that the scammer had been identified as @DVincent_ through doxxing via an exchange. According to the tweet, the total value of the items stolen by him (her?) reached around $2M.
Dollar and other Proof Collective members have already filed a report to the FBI; however, in his tweet, Dollar gave the crook a chance to avoid jail by delivering the stolen NFTs back.
In the commentaries to Dollar’s message, other users confirmed that the alleged scammer has also tried to lure them into selling NFTs while insisting that the deal had to be stricken on a questionable peer-to-peer exchange.
The Twitter page of @DVincent_ is already inaccessible. Well, of course!
Proof Collective is a mysterious private club of non-fungible tokens collectors founded by Kevin Rose. To become a member, one must own a Proof Collective NFT. The membership fee is high enough to scare off random passers-by: 88 ETC which is more than $200 000, at least it was so in May 2022. Proof Collective is most famous for Moonbirds, a highly-hyped NFT campaign (selling 10 000 owl avatars for 2.5ETC each) launched on April 16, 2022.