These days, the smartphone is more than just a means of communication. Every day we use it to communicate with friends and family, message social networks, browse the web. There are also more specific tasks – accessing our bank account, online shopping, taking photos and videos, streaming, and much more. Your smartphone is the key to most of the aspects of your daily life. Next we will tell you about smartphone security.
Our smartphones store vast information about us – our passwords, banking details, history of calls, messages, and pages visited. Consequently, the security risks that potentially threaten your accounts from criminals are not limited to hackers. Anyone who finds your phone if it’s lost or stolen can easily use your information in their not-so-noble interests. So here are five simple tips for keeping your smartphone secure. These tips are always relevant, whether it’s a phone you just bought or one you’ve used for years.
1. Always apply the last software updates and security patches
This is the easiest thing to do when buying a new smartphone. Most Android or iOS smartphones prompt you to download the latest operating system update when you first set it up. We recommend not delaying or canceling this action, as it eliminates cybersecurity vulnerabilities detected in the operating system. Saying short, applying updates prevents cybercriminals from exploiting known security problems. In addition, updates often optimize the operating system and add new useful features. Since most smartphones prompt you to install updates and only have to click “ok” or “cancel”, even a novice user can handle the process.
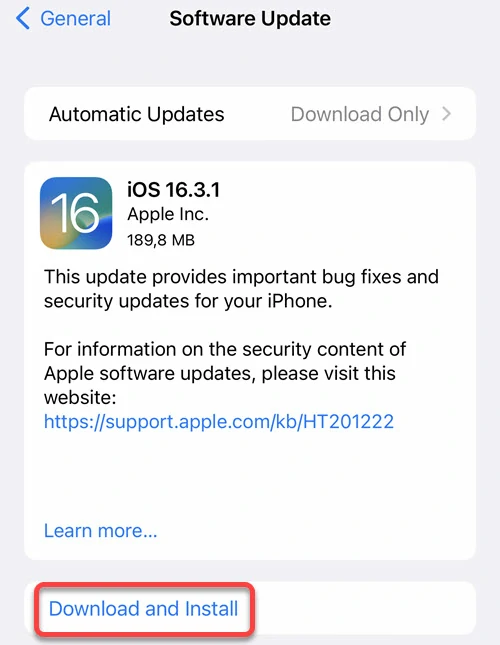
Most manufacturers keep their devices updated for as long as possible. However, some vendors could cease releasing security updates if your smartphone model is over a few years old. Since there is no standard for device shelf life, each manufacturer decides how long a device will receive updates. This time can vary from two to five or six years. To see if your smartphone still receives updates, you can visit the website of its manufacturer or send a query to their technical support.
2. Use a password, PIN, or biometric security features to protect your smartphone
We are usually serious about choosing a password to protect our email account or a PIN to protect our online banking information. However, when using a password to smartphone security, many prefer easy-to-guess passwords of four identical digits or don’t use screen locking. Of course, it’s much more convenient to pick up your phone and start using it right away than typing a password or PIN each time. However, it also means that if someone gets their hands on your smartphone, they can help themselves with its contents without obstacles. That way, anyone who finds it can easily access your data.
Although there is a slight chance that the person who found your device will use this information for good and return your phone to you, it is unlikely. Since criminals are looking to profit in any way they can, sharing your phone with them is not a brilliant idea. You will most likely lose access to your accounts, and your personal data will be compromised. For that reason, any applications you use to access sensitive information (such as online banking) should be protected by unique, secure passwords. It is essential to understand that these passwords should not contain your date of birth or be the same as the passwords you use to lock your phone.
3. Use multi-factor authentication if possible
Passwords are essential to protect your accounts, and they are one of the most sought-after pieces of information for cybercriminals. Knowing someone’s account password allows attackers to use it as if they were real users. They can send messages to the victim’s friends, view the victim’s social media profiles, and access documents and photos searching for sensitive personal information, such as banking information. On the other hand, if you use a relatively weak password, hackers can easily guess it using a brute force attack.
However, even if your password is strong enough, another danger exists. For example, the password may be stolen due to a phishing attack aimed either at you or the company managing the account. In the first case, the blame lies entirely with you. Another case, however, renders the company whose services you use guilty of the leak. In 1995, AT&T invented multifactor authentication (MFA) to prevent this from happening. The technology’s essence is the user’s additional confirmation of the attempt to log in to his account. For example, suppose your password was somehow compromised. If you’re not using MFA, an intruder would enter your login and password and log in to your account. However, if you are using MFA, the attacker cannot directly access your account. Instead, you’ll get a warning that someone is trying to log in.
What should I do if I received a message?
You should log in immediately and change your password if you did not do this. Next, you should also forcibly end other active sessions. You can do it from the browser. Suppose you want enhanced security. In that case, you may consider using a physical security key, perhaps the best way to protect your data. This form of multifactor authentication assumes that you need a key that you own to access your accounts. Unlike confirmation codes or SMS, which, although difficult but possible to intercept, you need the attacker to hold the physical security key to pass this protection. It’s only possible if they manage to steal it directly from you.
iPhones running iOS 16.3 or later allow you to use security keys for your Apple ID. So you can use a hardware key as an additional level of authentication. Such security keys are tied to your Apple ID and require your username, password, and a hardware key to access your account or device. While MFA provides an excellent extra layer of smartphone security and accounts protection, it’s worth remembering that it’s not wholly infallible.
4. Download applications and updates from trusted sources only
As a regular user, you are probably satisfied with downloading apps from the official app store. Those are Google Play Store for Android and App Store for iPhone. By default, they are considered the only proper place to download apps. However, there are reasons why users are not happy with such download methods. Most commonly, people are looking for an alternative way to install the required application on their smartphones for free, i.e., use cracked apps. Unfortunately, this is a bad idea because any “free” versions come from a third-party site, which can expose you to a security breach.
Scammers and cybercriminals never disdain such a niche. They are well aware that people tend to prefer free versions of many popular apps, unlike smartphone security. That’s why scammers often promote websites they own in search and buy ads to promote their malicious sites. The main danger of fake sites is that a program you get from them may be in fact a trojan virus. Aside from that, the app you download from such websites may not work properly or fail to start. In addition, it is a way to trick you into downloading malware or snatching your username and password.
Download apps with caution
Unfortunately, although official app stores are considered safer than third-party sites, and rightly so, sometimes malicious apps do bypass official store protection and become available for download. Therefore, you should be sure about what you are downloading. In addition, we recommend you check what permissions the application you are installing asks for; this directly affects smartphone security. Seeing that calculator asks to access your contact book and gallery is a bad omen. You can also check reviews. If something is wrong with the program, you will find it out there.
Another method of spreading malicious downloads is phishing emails that warn the user about a problem with a frequently used app or that the subscription is about to expire and a request to update the app. Legitimate apps will never ask you to download an update via email. Instead, when the developer releases an update to an installed app, the app store will update the app itself. If you have the auto-update feature turned off, you’ll either get a notification from the app store or the app will ask you to update itself when you launch it.
5. Use VPN when using public networks
Today, most mobile operators provide tariff plans with large amounts of 4G or 5G traffic. This allows you to do whatever you used to, without worrying about running out of traffic. However, some thrifty users, seeing a public Wi-Fi network, will prefer it. While many free wireless hotspots are safe and legit, they carry privacy risks. Using a public Wi-Fi network means data transfer is less secure than a cellular connection or on your home or corporate network.
There’s nothing wrong with connecting to public Wi-Fi, but it is essential to understand the risks when you do. You should also be careful about what information you enter and transmit on public Wi-Fi networks. If possible, avoid entering passwords or any sensitive information. Any trickster can intercept your data during the course of a man-in-the-middle attack. If you urgently need to log into your bank account, it will be a good idea to find another way to accomplish that.
The danger is that savvy scammers often set up their open Wi-Fi networks in busy places, allowing people to connect to them. This way, scammers can monitor the transmitted data and intercept your logins, passwords, bank details, and other personal information. However, consider a mobile VPN if you need to transfer sensitive data. Because it encrypts your data, it can better protect it while keeping your Internet use private.