The Cybersecurity and Infrastructure Security Agency (CISA) recently issued an alert about an actively exploited critical vulnerability in Palo Alto Networks’ Expedition software. This tool, typically used for migrating firewall configurations from other providers like Checkpoint and Cisco to Palo Alto Networks’ PAN-OS, has been found to have a significant security flaw. Hackers use it for taking over administrator accounts, and consequently gaining access to the entire environment.
Vulnerability Details and Exploits
The vulnerability, known as CVE-2024-5910, is a missing authentication flaw that Palo Alto Networks patched in July. This flaw comes from the mechanism of access controls: a part of the code responsible for verifying the user identity is not implemented properly. This, in turn, allows attackers to remotely access Expedition servers exposed to the internet and reset administrator credentials without authorization.
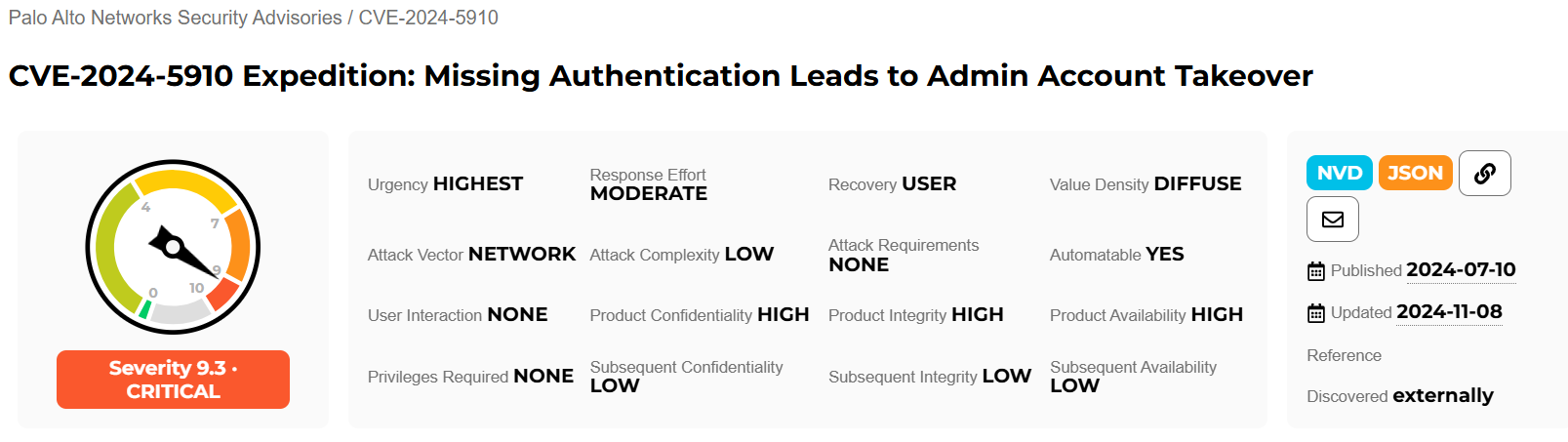
Such a takeover leads to gaining access to sensitive data, like as configuration secrets (data that describes how the firewall operates), and credentials (usernames, passwords, and API keys). With that data, hackers can easily plan their lateral movement, and have all the tools to disable potential obstacles.
Expanding the Attack with Command Injection
In October, security researcher Zach Hanley from Horizon3.ai released a proof-of-concept exploit—essentially a demo of how the vulnerability could be used in a real-world attack. Hanley’s method shows how CVE-2024-5910 can be combined with another vulnerability, CVE-2024-9464, which is a command injection flaw.
A command injection vulnerability allows attackers to run unauthorized commands on a system by exploiting weaknesses in software validation. This command injection exploit provides a pathway for attackers to execute arbitrary commands (any commands they choose) without needing credentials. As a result, effectively gaining full control over vulnerable Expedition servers.
CVE-2024-9464 and related vulnerabilities also allow for unauthenticated arbitrary command execution. I.e. attackers don’t need a valid username or password to launch their attack. By chaining these vulnerabilities together, attackers can target not just the Expedition tool, but also gain access to firewall admin accounts on PAN-OS (Palo Alto Networks’ firewall operating system).
Official Action and Mitigation Measures
In response to the active exploitation, CISA has added CVE-2024-5910 to its Known Exploited Vulnerabilities (KEV) Catalog. This catalog lists vulnerabilities confirmed to be used in real-world attacks, alerting organizations to prioritize their remediation.
As part of the binding operational directive (BOD 22-01) issued in 2021, U.S. federal agencies must secure any vulnerable Expedition servers on their networks by November 28, within a three-week deadline. This requirement is part of an ongoing federal cybersecurity effort to quickly address and mitigate known security risks.
Palo Alto Networks also advises all Expedition administrators to rotate usernames, passwords, and API keys (generate new ones) after updating to the fixed version of the software. Any credentials processed through Expedition should also be rotated to reduce the risk of compromise from previous, unpatched versions.
For organizations unable to apply the necessary patches immediately, CISA recommends limiting network access to the Expedition tool by restricting it to only authorized users or trusted networks. This approach, called network segmentation, ensures that only specific individuals or systems can access critical tools.