On December 3, 2023, ALPHV ransomware gang claimed hacking into a fintech software provider Tipalti, Roblox and Twitch, its clients. The approach, however, appears to be unusual, as the gang created a listing that says “but we’ll extort Roblox and Twitch, two of their affected clients, individually”. Criminals promise to publish updated posts on Monday morning, which will maximize the stock price impact.
Tipalti Hacked, Roblox and Twitch are Collateral
On Saturday, December 3, 2023, ALPHV came out with quite an unusual claim. Hacker group talked about hacking into the network of Tipalti, a payment automation and accounting software provider, back in early September 2023. The text below is the quote taken from their Darknet leak site:
Thing is – the company itself did not receive any ransom note yet. The typical practice in cyberattacks is notifying the victim via ransom notes, and only then publishing info about the hack. Though not this time – as hackers say, they doubt the co will contact them back due to some specific details they discovered while being active in the network.
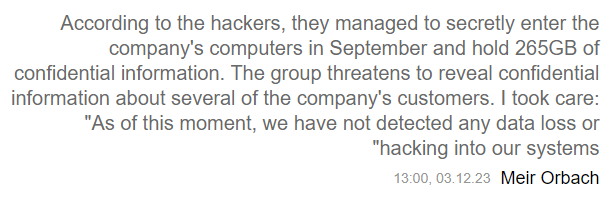
Another detail the hackers uncover is the involvement of an insider. Well, this is not a rare occurrence, but threat actors rarely speak openly about this. And in the context of several companies taken as collateral, this sounds more like an attempt to ruin the company’s image. That especially contrasts with the official response of the company, given to the Israeli media Calcalist.
Roblox and Twitch Fall Victim to Tipalti Hack
The worst part about this hack is that hackers managed to compromise two client companies, namely Roblox and Twitch. Actually, Roblox is not the first time a victim of a ransom hack – the same ALPHV gang hacked them in 2022. Twitch though is mentioned only in the listing title, without any further references in the text. This may be the sign of less than significant amount of data the hackers managed to leak.
At the same time, some serious threats faced towards Roblox appear in the text. Hackers say they will publish the data of more victims (supposedly other Tipalti clients) in the months to come. To avoid this from happening, both mentioned companies should pay the ransom. They either do not specify any sums and, what is more important, types of data leaked from the game developer.
Is it that dangerous?
Despite how threatening all the situation looks, I’d take it with a grain of salt. Hackers often exaggerate the total damage, especially when it comes to collateral damage. Claims about Tipalti’s clients being hacked are most likely just the attempts to scare all the involved parties and make them pay.
What is out of doubt though is hackers’ access to some of the data. In particular, they are not likely to lie about their access to the major amount of Tipalti’s data. For other companies though it is most likely some data about financial transactions – things they actually delegated to Tipalti. However, this is still not great, as such info leakage may be the reason for companies to switch to a different service.
To sum up, despite touching a whole array of companies, the hack brings the most harm to Tipalti. And mostly reputational: even if not a lot of clients’ info ended up in hackers’ hands, the fact of the leak persists. The obvious conclusion is to avoid deep integrations with such unreliable companies, just to minimize the possible damage in the case of another cyberattack.
UPD 12/05/2023
The original listing you could have seen above was changed for a more classic one, that claims Tipalti hack. However, threat actors still use the text note as a place for a post-scriptum note. Criminals disprove Roblox’ claims regarding absence of any signs of network compromise saying that they will contact them later.
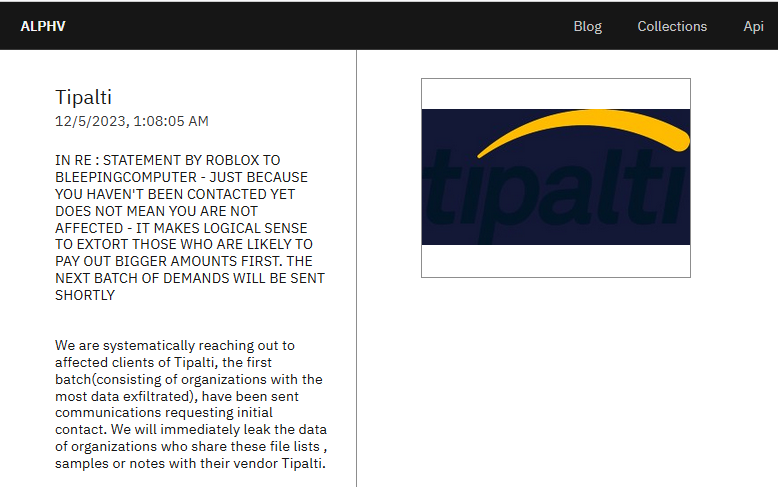
At the moment, ALPHV hackers claim to be contacting the first group of Tipalti clients who got their info leaked during the hack. Though they do not contact the company itself, saying they are going to reach out to the clients first. Another interesting detail unveiled after the re-listing is the fact that no ransomware was used – they just leaked 265 gigabytes of data.