Trojan:Win32/Casdet!rfn is a detection that indicates the possible presence of malware on your system. Users may encounter this detection after using pirated software or opening suspicious email attachments. In certain cases, Casdet may be a false positive detection.
Casdet is a severe threat mainly used for reconnaissance and delivering other payloads to the device. It also collects some data about the system but can be modified for different tasks, such as direct information theft.
Trojan:Win32/Casdet!rfn Overview
Trojan:Win32/Casdet!rfn is a detection that Microsoft Defender mainly uses for remote access trojans (RATs). Such malware, as its name implies, provides remote access and is often used for reconnaissance and delivery of other malware. Casdet doesn’t usually collect a lot of information, but the payload it carries is what does the most damage. Aside from this, Casdet has a modular structure, which allows it to dynamically plug in modules it needs and act as an information stealer, for example.
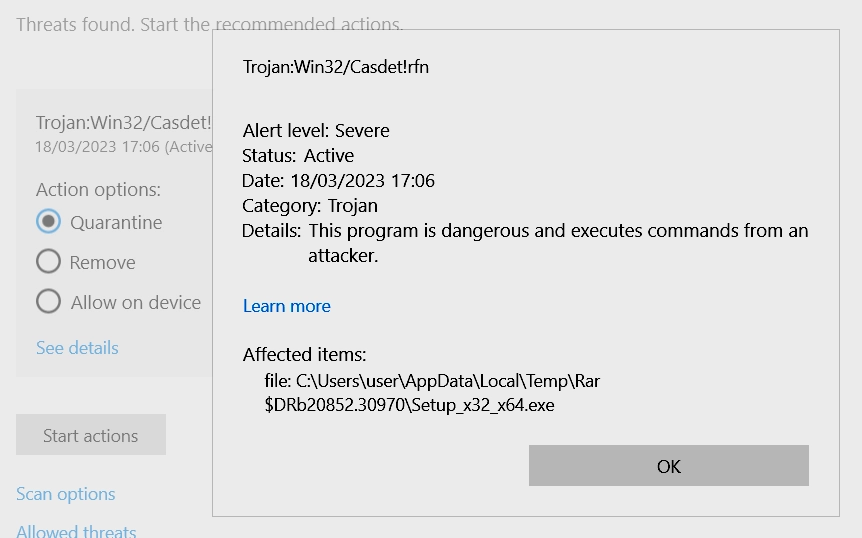
Trojan:Win32/Casdet!rfn is usually spread via phishing emails and cracked software, spread through p2p networks. Rarely though it can turn out as a false positive, marking a legitimate file as malicious. Some users have complained about Trojan:Win32/Casdet!rfn detection after downloading and installing a legitimate Android emulator, e-books, or game mods. Let’s take a detailed look at how this malware works.
Detailed Analysis
To remove Trojan:Win32/Casdet!rfn, I recommend using GridinSoft Anti-Malware. This program is resilient to the anti-detection techniques this malware uses, thanks to its multi-component detection system.

Download and install Anti-Malware by clicking the button below. After the installation, run a Full scan: this will check all the volumes present in the system, including hidden folders and system files. Scanning will take around 15 minutes.
After the scan, you will see the list of detected malicious and unwanted elements. It is possible to adjust the actions that the antimalware program does to each element: click "Advanced mode" and see the options in the drop-down menus. You can also see extended information about each detection - malware type, effects and potential source of infection.

Click "Clean Now" to start the removal process. Important: removal process may take several minutes when there are a lot of detections. Do not interrupt this process, and you will get your system as clean as new.
