100% disk usage is a widespread problem among Windows users that has several possible origins. Having your disk 100% loaded is unhealthy and leads to PC usage problems. Let’s figure out which problem causes 100 disk usage Windows 10 and troubleshoot it step-by-step.
Why is my disk at 100?
High disk load is a problem with many possible sources. Disk, 100% load, means that works at its peak read/write speed. Alternatively, it just doesn’t work properly – so the computer fails to read or write the required data. Normally, the operating system will never use so much of your disk unless the problems happen. However, we will check out the possible software and hardware problems in the next chapter. The most common visible effect of having your disk drive overloaded is a very long response time of any operation on your computer. All launched apps will likely freeze at the moment of peak disk usage. Aside from the PC slowness, you may also spectate the inability to open any folder in your file system. In other words, your PC becomes useless, and it requires an urgent fix.
Fixing the disk 100% load
As I mentioned, there are several reasons for disk overload. During the troubleshooting, it is important to define it correctly and completely – otherwise, the effect will only be partial, or there will be no effect at all. By the depth level, issues can be divided into software, firmware, and hardware.
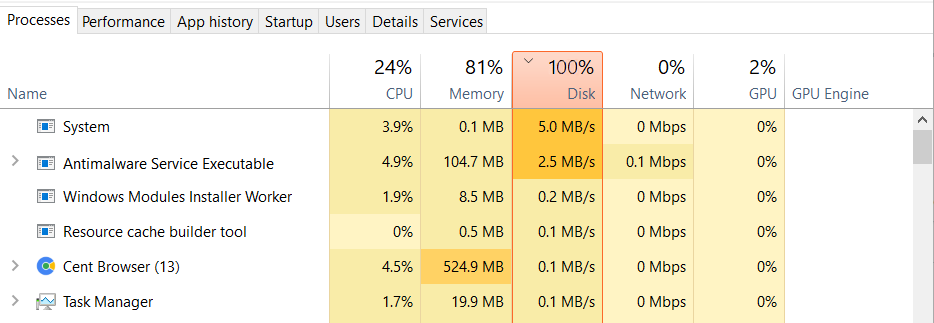
Software issues that cause disk 100%
Software issues stand for the situations when Windows 10 disk 100% usage appears during the normal usage of certain applications. That possibly can be the intended behavior of the application. For example, disk check-up tools and anti-malware software are forced to take the max disk read/write speed to provide the max performance. But more often, programs will put your disk at 100 because of optimization issues or bugs. You can easily uncover this source of the problem by opening the Task Manager. The only app that takes the vast majority of disk capacity is what causes the overload.
Troubleshooting the software issues
Reporting the issue to the developer will probably help – they may consult you on decreasing the disk load. If the problem appears because of the program malfunctioning, the developer will probably issue a bugfix soon after. However, if you discover that the problem is only yours and no one can repeat it, you should go to the next step.
Summary for software troubleshooting
- Detect the application that takes too much disk capacity
- Try using it in a different mode
- Contact the developer to get help with troubleshooting
- If the problem is not related to the program – go to firmware issues troubleshooting
Firmware issues
Firmware, or more precisely, the drivers for your storage devices, are very important for the correct device work. Drivers instruct the OS on how to interact with the device. And as you can guess, wrong or outdated instructions can lead to issues like disk 100% load. In some situations, the problem can be in several places simultaneously. Disk drivers can conflict with drivers of another device you use, causing serious problems with their coexistence. The latter frequently happens when you use exotic equipment or old devices.
To solve firmware issues, you first need to install the disk’s most recent version of drivers. It is strongly recommended to get them from the manufacturer’s website. Primarily, you need to find the specifications for your disk, at least its family name. After that, search for the drivers for your device on the manufacturer’s website. Remember that you should get it exclusively from the manufacturer – otherwise, there is a big risk of repetitive malfunctions and malware.
Some vendors also offer monitoring tools for their product lines. That makes life much easier, as these utilities also show the disk diagnostics information and will help uncover possible hardware issues.
Fixing the driver conflicts
The aforementioned situation when the disk overload happens because of the driver conflict requires more steps to fix. Aside from the driver issues of the same disk, you also need to troubleshoot the devices that are interacting with the disk. In particular, those devices could be RAM extension units (like Optane modules) or RAID arrays.
RAM extension units sometimes work wrong on motherboards that are not 100% compatible with such modules. For sure, the manufacturer should likely have a license for using such technologies, but there are still a lot of copies based on reverse-engineering present on flea markets. Using surrogates of this kind with original equipment can create problems with both hardware compatibility and driver conflicts. To understand if it causes such an issue, plug out the extension module, and try to boot your PC once again. Remember that this device must be detached only after the complete shutdown of the computer.
Troubleshooting
Fixing the conflicts between extension modules may involve updating both drivers for this module, motherboard firmware, and storage device drivers. Searching the corresponding drivers and firmware on the manufacturers’ websites and installing them will likely solve the problem. However, if you use the no-name motherboard from Aliexpress that supports this technology, the problem may hide in the hardware incompatibility of this module. Therefore, only cease extension module usage or change the motherboard on the one with official support.
RAID arrays belong to the other kind of problem sources. Complicated hardware conjunction is relatively hard to set up, and the problems like 100% disk usage Windows 10 is an often cases when something goes wrong. In that situation, follow the RAID setup guidelines until you get the system working without any problems.
Step-by-step summary for firmware problems solving
- Update the disk drivers
- Update the motherboard firmware
- Update the drivers of memory units (RAM extenders/ROM)
- Disable the units that may possibly cause conflicts & high disk load
- Go to hardware issues troubleshooting
Hardware issues that cause 100% disk
The most unpleasant reason for Windows 100% disk usage is when something goes wrong with the hardware. There are many more places where something can get wrong, and fixing it is rarely possible. Fortunately, hardware problems are a pretty rare reason for the disk’s 100% usage. If you tried all other troubleshooting methods and they did not have any effect, the problem is likely hidden in the hardware. The possible hardware sources for 100% disk usage are problems with the connection interface, connection adapters (IDE to SATA, Flash to IDE, etc. ), and the exact disk.
Troubleshooting the connection interfaces & adapters
The connection interfaces and adapters issues are easiest to resolve. SATA cables are pretty cheap and widespread, so first, purchasing a new pair of ones is recommended. One cable is for the power supply, and the other – is for data transfer. It is better to substitute both to eliminate any possible issues. The additional sign of problems with the connection interface is sporadic disconnections of the disk – it may randomly appear and disappear from the list of storage devices.
It is slightly harder to solve the hardware issues with disks that use PCIe and M.2 connection interfaces. In the case of PCI Express, you can try to plug the disk into a different port on the motherboard – but there could be no free PCIe ports. M.2 slot is oftentimes represented as a single available slot of this connection interface on the motherboard. In the latter case, the only way to figure out the problem is to plug it into the other computer with this slot on the motherboard.
If changing the connectors or trying a different slot does not give you a good effect, and you still see your disk running at 100%, the problem is likely inside of the disk.
Troubleshooting the disk issues
Generally, disk issues are not always related to malfunctioning. Some of the old HDD variants may have such a low read/write speed that modern programs will easily overload it. But the probability that you use such an old disk is pretty low. A much more common case is when something goes wrong with the exact drive or with its controller. You can only diagnose the problem with your disk – fixing it requires special equipment, or maybe even impossible.
For HDDs, a reliable sign of a disk malfunction is any kind of scratchy or tinkling noise. Hard disk drives have their own noise – the spindle rolling at around 7000 RPM – but it sounds rather like a rustle. Mechanical noise means that moving parts inside of the disk – read/write heads and platters – collide with each other, thus damaging the platters that contain the data.
SSD is harder to troubleshoot since there are no visual signs to recognize the malfunctioning drive. The only way to ensure that there is a problem with the exact disk is to plug it into the other computer. If it keeps showing you a high disk load – the problem is likely there. You can bring it to the service center; you may be saved if the problem is inside the disk controller. But fixing the exact storage cells is very difficult and just irrational. To ensure that the disk is the source of a problem, you can scan it with disk scanning programs. I recommend a free program with a two-decades-long reputation – Victoria. It will easily uncover the disk wearing, which is impossible to see with your eyes.
Hardware issues fixing instruction
- Check-up the connection interfaces
- Try to plug the disk into the other PC
- Check the disk for mechanical damage
- Check the disk for wearing with disk scanning tools
- Bring the disk to a service and purchase a new one