Google TAG’s recent discovery reveals a 0-day exploit, CVE-2023-37580, targeting Zimbra Collaboration. This is a Cross-Site Scripting (XSS) vulnerability exploited in four campaigns.
Zero-day discovery was patched
A severe vulnerability has been discovered in the Zimbra email software. Four hacker groups exploited vulnerabilities to steal email data, user credentials, and tokens. According to the Google TAG research, most attacks were reported after the company published an initial patch on GitHub.
The vulnerability, CVE-2023-37580, with a CVSS score of 6.1, is a cross-site scripting (XSS) vulnerability present in versions before 8.8.15 Patch 41. The company has addressed the issue as part of the updates released on July 25, 2023. The flaw can be exploited to execute malicious scripts in a victim’s web browser via an XSS request after simply clicking a URL link. The worst part is that you don’t need to download or install anything for the attack to succeed.
Exploitation Overview
In June 2023, researchers reported multiple waves of cyber attacks. The attacks began on June 29, at least two weeks before Zimbra released the official notice. Three of the four malicious campaigns were discovered before the patch was issued. At the same time, the fourth was detected a month after the patch was published.
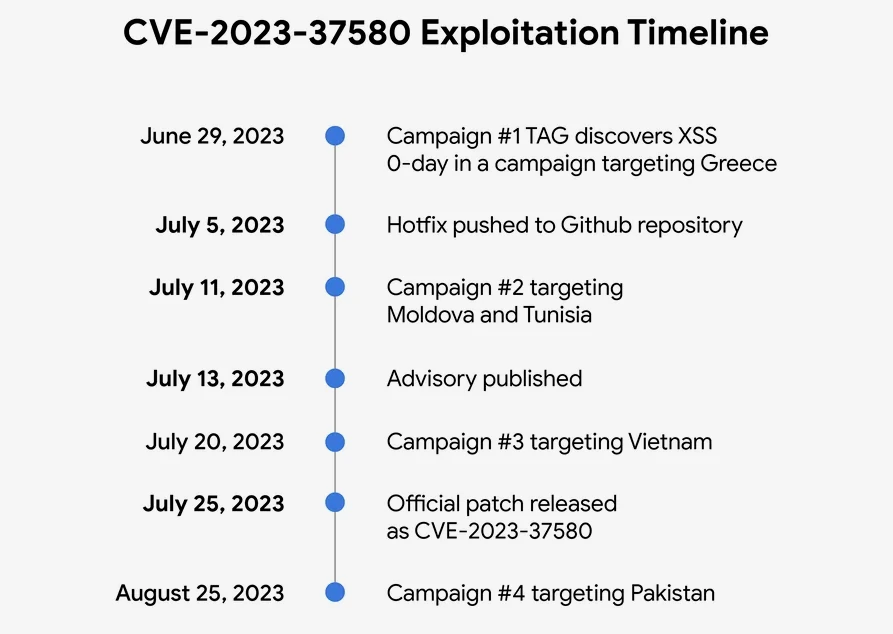
Greece Targeted for Email Theft. The initial exploitation targeted a government organization in Greece, employing emails with exploited URLs. Clicking the link during a Zimbra session led to the deployment of a framework documented by Volexity in February 2022. This framework utilized XSS to pilfer mail data, including emails and attachments, and set up auto-forwarding to an attacker-controlled email address.
Winter Vivern Exploits after Hotfix. Following the hotfix on July 5, an actor exploited the vulnerability for two weeks starting July 11. Multiple exploit URLs targeted government organizations in Moldova and Tunisia, attributed to the APT group Winter Vivern (UNC4907). The vulnerability facilitated the loading of malicious scripts.
Phishing Campaign in Vietnam. Days before Zimbra’s official patch, an unidentified group exploited the vulnerability in a campaign phishing for credentials in a Vietnamese government organization. The exploit URL is directed to a script displaying a phishing page for webmail credentials.
Authentication Token Theft in Pakistan. After the CVE-2023-37580 patch release, a fourth campaign targeted a government organization in Pakistan, focusing on stealing Zimbra authentication tokens, exfiltrated to ntcpk[.]org.
Safety Recommendations
As we can see, attackers often closely watch open-source repositories. Thus, they continuously look for vulnerabilities that they can exploit. In some cases, the fix for a vulnerability may already be available in the repository but not released to users.
CVE-2023-37580 could allow an attacker to steal user data or take control of user accounts. Upgrade to Zimbra Collaboration (ZCS) 8.8.15 Patch 41 or later to avoid this vulnerability. If you cannot upgrade immediately, you can mitigate the risk of this vulnerability by disabling the Zimbra Classic Web Client and using the Zimbra Web App instead.