Today, in the constantly changing world of cyber threats, attackers always look for new ways to get more benefits with less effort. Recently, researchers found an example of this and called it proxyjacking for profit.
What is proxyjacking?
Proxyjacking is an attacker’s illegal use of a victim’s bandwidth for its own good. The closest related process to proxyjacking is called cryptojacking. It involves an attacker illegally using the victim’s device power to mine cryptocurrency. There is nothing new under the sun, and although proxyjacking has been around for some time, it is only now that attackers have begun to use it so brazenly for profit.
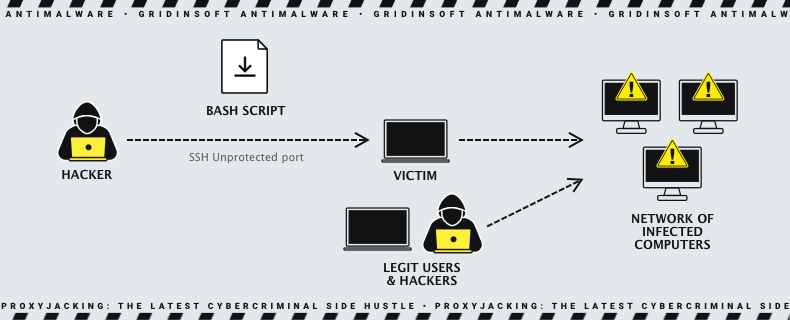
First of all, cybercriminals can use proxy servers to cover their tracks. This makes it difficult to trace their illicit actions back to their origin by routing malicious traffic through multiple peer-to-peer nodes before reaching their final destination. Experts have found that financially motivated criminals actively attack vulnerable SSH servers. They aim to discreetly turn them into a proxy network, which they then rent out to other criminals. Because proxyjacking has little or no effect on overall system stability and usage, it is harder to detect.
Diving into details
Experts discovered these attacks on June 8, 2023, after hackers established multiple SSH connections to honeypots managed by the Security Intelligence Response Team (SIRT). By connecting to one of the vulnerable SSH servers, the hackers deployed a Base64 Bash script that added hacked systems to Honeygain or Peer2Profit. The script also deployed a container, downloading Peer2Profit or Honeygain Docker images and eliminating competitors’ containers, if any were found. In addition, researchers found cryptojacking miners, exploits, and hacking tools used to store the malicious script on the compromised server. In other words, the attackers either switched to proxyjacking or used it to generate additional passive income. Now we’ll explain in detail how it happened.
1. Penetration
By controlling a honeypot, experts could monitor the actions of attackers who used encoded Bash scripts. The attackers utilized a double Base64-encoding technique to obscure their activities. However, the researchers successfully decoded the script and gained insight into the attacker’s proxyjacking methods. Through careful analysis, they could understand the attacker’s intended operations.
2. Deploying
Thus, the compromised system transforms into a node in the Peer2Profit proxy network. Now it is using the account specified by $PACCT as the affiliate that will benefit from the shared bandwidth. The same was discovered for a Honeygain installation shortly after. The script is designed to be discreet and sturdy, attempting to operate regardless of the software installed on the host system. The script begins by defining a few functions for later use, including a basic curl implementation. This is then used within the second function to download an actual curl version (hosted on the distribution server as “csdark.css”). If curl is not present on the victim host, the attacker downloads it on their behalf, as it is all required for this scheme to work.
3. File analysis
The analysis shows it’s a basic curl version without significant modifications. Nevertheless, it may have additional features, but no evidence of harm exists. However, the ability to look at the source of the artifact explains it was part of a proxyjacking scheme. It emphasizes the importance of identifying all unusual artifacts. Next, the attacker creates a function that moves to a writable and executable location. If no appropriate directory is found, the executable terminates.
4. Eliminating competitors
The script has a final function that sets up the bot. However, this function is commented out in the main script and replaced with possibly more effective code. Most of the action happens in the rest of the code, with some parts redacted. The script starts by checking if its container is already running and then proceeds to kill any rival containers that are also sharing bandwidth. This process is repeated to ensure that no other rival containers are running.
Distribution server
Researchers traced an attack and discovered a compromised web server in Libya that distributed components for attacks. The server had outdated and unmaintained components, including a library called metro-bootstrap. Three files were last modified in 2014, while newer files suggested the server had been compromised. Researchers used `wget -r` to download all files for analysis. The csdark.css file was uploaded, followed by metro-bootstrap.min.xcss, and then vksp, which was later found to be a Linux-specific crypto-miner named perfcc. Analysis revealed that vksp contained a crypto-mining utility, exploits, and hacking tools. That suggests a pivot or supplementing of cryptojacking with proxyjacking. Hosted on the same website, these executables provide proof of actors who will capitalize on this monetization strategy.
Why do they do it?
In this campaign, Peer2Profit and Honeygain were the two P2P proxy monetization schemes discovered. Both have public Docker images with over 1 million downloads. Unfortunately, some potentially unscrupulous companies use these proxies for data collection and advertising, even though they are technically legitimate. Some companies allow users to see precisely how their traffic is being used. While these applications are not inherently harmful and are marketed as voluntary services that offer compensation in exchange for sharing unused internet bandwidth, some companies fail to properly verify the sourcing of the IPs in their network. Sometimes, they even suggest installing the software on work computers, which is risky.
How to avoid proxyjacking?
Initially, a proxy server is perfectly legitimate. Each user is free to provide bandwidth for any purpose. However, if this process occurs without the user’s knowledge, it becomes a cybercrime. Preventing unwanted things is not as difficult as it may seem at first glance. It’s enough to be cautious when using the Internet and adhere to the following recommendations:
- Use strong passwords. A strong password is the first line of defense. Therefore we recommend using a password generator to create a strong password. Also, you should avoid repeating the same password on different sites.
- Use two-factor authentication. Suppose your first line of defense is down. In that case, 2FA won’t let the attacker in further because he can’t access the confirmation code.
- Install all OS and software updates regularly. Software updates are patches for vulnerabilities through which attackers can also infiltrate your device.
- Use advanced anti-malware solutions. While a basic security tool satisfies most of the average user’s needs, you can use an advanced anti-malware tool. It’s a great addition to the Windows Protector and will protect your device from various attacks.