Analysts at Digital Shadows have prepared a report on the exploit market on the darknet – it is noticed that the criminals have come up with an “exploits as a service” scheme. Some cybercriminals have multimillion-dollar budgets to acquire 0-day exploits.
The researchers explain that attackers, financially motivated cybercriminals and “government hackers” are rapidly adopting new attack methods and are constantly on the lookout for new exploits.
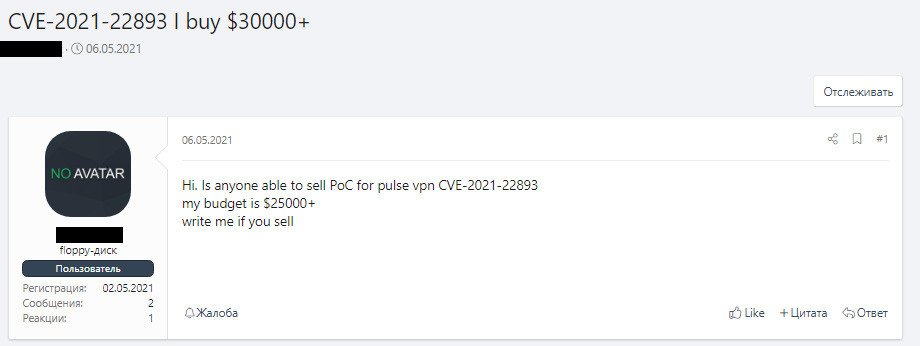
The researchers write that although most often buying and selling exploits occurs in private conversations, sometimes vulnerabilities are bought and sold directly on hacker forums. For example, in early May 2021, a hacker openly offered $25,000 for a PoC exploit for the CVE-2021-22893 critical vulnerability affecting Pulse Secure VPN. This problem has been used by Chinese hackers since at least April of this year.
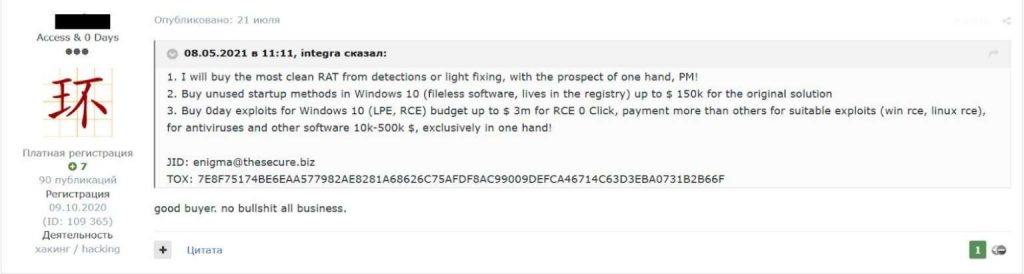
Another hacker even stated that he was ready to pay up to $3,000,000 for exploits for RCE vulnerabilities in Windows 10 and Linux, the use of which does not require any user interaction. The same user was offering up to $150,000 for previously unused methods of running malware on Windows 10, which would allow malware to remain active on every system boot.
For comparison, the well-known exploit broker Zerodium offers up to $1,000,000 for zero-click RCE in Windows 10. And most of all, up to $2,500,000, the company is ready to pay for a chain of persistent zero-click exploits for Android, and $2,000,000 for the iOS equivalent of such an attack.
Researchers at Digital Shadows say they have seen some hackers negotiate exploits for zero-day vulnerabilities at a cost of $10,000,000. Moreover, not only “government hackers”, but also by other cybercriminals, especially ransomware operators, can afford such deals.
However, this type of transactions are not easy and can be time-consuming. In this case, the developers of the exploit may lose the chance to make money, because if their competitors can offer their own version of the exploit and reduce the price. Digital Shadows writes that for this reason cybercriminals are actively discussing an “exploit as a service” scheme that would allow developers to lease such exploits to several parties at once.
As part of the report, experts from Digital Shadows divided the criminals into several groups, noting that there may be serious intersections between them.
- Major players: cybercriminals who buy and sell 0-day exploits at prices starting at $1,000,000. They can be sponsored by governments or successful entrepreneurs.
- Regular Vendors: Vendors selling non-critical vulnerabilities, exploit kits, and databases of information (names and IP addresses) of companies with open vulnerabilities.
- Regular Buyers: People with technical skills who are interested in buying exploits, but rarely have the means to make such a purchase. They usually wait for prices to fall.
- Code Promoters: Criminals who publish and advertise their exploits on GitHub.
- Demonstration Performances: Highly specialized forum members who discuss bugs, take part in competitions, and share some knowledge about how exploits work.
- Newbies: The least trained users who learn from the more experienced forum members. Sometimes they apply the knowledge gained in practice and share information in other forums in order to earn a reputation, or in the framework of “social activities”.
- Newsfeeds: Forum members who share articles and news about recently discovered vulnerabilities with other articles and news.
Let me remind you that I also wrote that Experts published a list of the most attacked vulnerabilities in 2020-2021.