Experts from York University explained how they managed to detect vulnerabilities in popular password managers. Bugs allowed malware stealing user credentials.
It turned out that back in 2017, researchers analyzed five popular password managers: LastPass, Dashlane, Keeper, 1Password and RoboForm. The analysis helped identify four previously unknown vulnerabilities, including one that led to the disclosure of credentials.
Therefore, the most serious of the detected problems allowed the malicious application to impersonate a legitimate program and trick the password manager into revealing the stored credentials. Experts did not risk talking about their research before, as they considered it too dangerous.
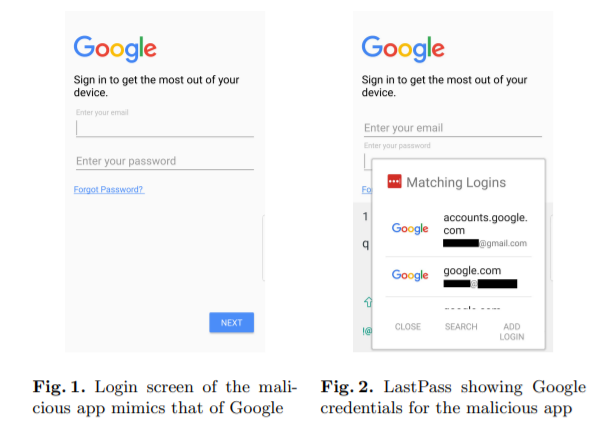
“The main problem affected the Android applications 1Password and LastPass, which were recognized as vulnerable to phishing attacks, as it was very strange to determine which saved credentials to offer for autocomplete. In fact, a malicious application could pretend to be legitimate simply by using an identical name”, – write the experts.
So, the researchers created a PoC application that successfully attacked LastPass (and could do the same with 1Password). This application had a login screen designed to mimic the official Google login screen, and therefore was difficult to distinguish from the real one. As a result, LastPass offered for this fake auto-complete with Google credentials.
At the same time, experts note that the attack had a number of obvious limitations: the malicious application must be installed on the victim’s device, and the victim herself must use vulnerable password managers and autocomplete, and also have credentials for the target application stored in encrypted storage.
Another vulnerability that researchers found in all of the password managers listed above (with the exception of 1Password) was that they did not provide sufficient protection for the credentials copied to the clipboard. In particular, in Windows 10, credentials could be pasted from the clipboard in plain text, even if the computer is locked. According to experts, to protect against such attacks, password managers should be able automatically clear the clipboard after a certain time.
Although some password managers allow users to protect their password store with a four-digit PIN code, experts write that RoboForm and Dashlane applications did not have a counter of the number of incorrect attempts to enter this code. That is, an attacker could sequentially enter two PIN codes, then remove the application from the list of recently used ones and try two more PIN codes. Even if an attacker enters PIN codes manually, he can still pick up a PIN code in an average of 2.5 hours.
“We did not fully automate this attack, but we believe that in the case of an automated attack, PIN retrieval will take significantly less time”, — experts write
Researchers contacted the developers of the tested password managers back in 2018. It is reported that five vendors responded to their requests and listened to warnings, but patches were not issued for all detected problems, as many of the vulnerabilities found were given a low priority.
Let me remind you that the popular password meter services put Internet users at risk. So, it remains only to remember passwords, right? )