VMware, a key player in virtualization services, is reaching out to users about a critical security issue in its Cloud Director. Tracked under CVE-2023-34060, this vulnerability, with a CVSS score of 9.8, specifically affects instances that have undergone an upgrade to version 10.5 from previous versions.
VMWave Cloud Director Vulnerability Allows for Unauthorized Access
Discovered and reported by Dustin Hartle from Ideal Integrations, the vulnerability exposes users to unauthorized access by circumventing authentication protocols. VMware is stressing the urgency, underscoring the use of a vulnerable version of sssd from the underlying Photon OS.
This announcement follows VMware’s recent endeavors to tackle another critical flaw (CVE-2023-34048) in the vCenter Server. It highlights the persistent challenges in the ever-evolving cybersecurity landscape.
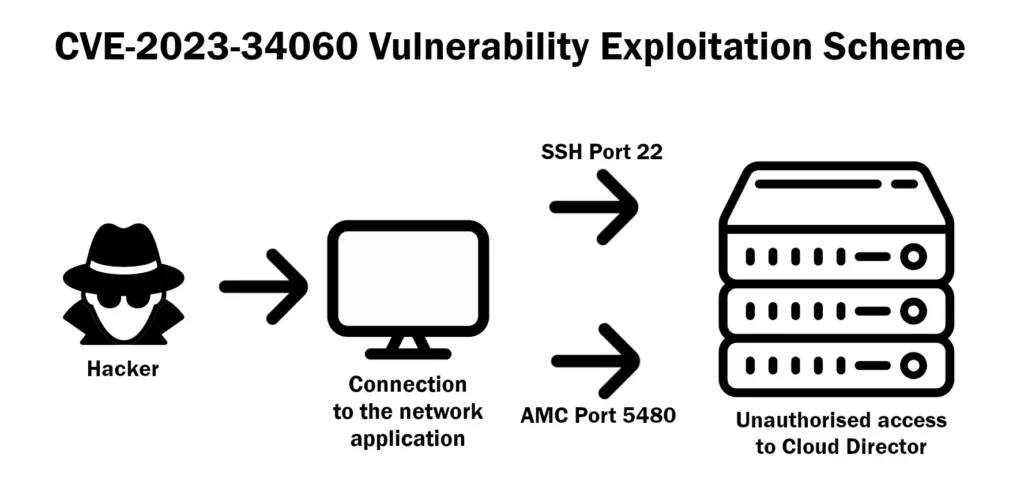
The potential impact of this vulnerability extends beyond the technical realm—it sparks concerns about unauthorized access to critical systems. VMware clarifies that, currently, there’s no immediate threat to flight security. However, the focus is squarely on mitigating potential risks related to data exposure.
Cloud Director Vulnerability Fixes Available
Currently, a critical authentication bypass vulnerability is present in VMWare for which a patch is not yet available. However, VMWare has released a Security Advisory VMSA-2023-0026 to guide administrators through the issue and the upgrade path that will solve it. Meanwhile, a temporary workaround for the affected versions of VCD Appliance 10.5.0 has been suggested.
VMware site
To apply this workaround, administrators can download a custom script attached to a knowledgebase article and run it on cells vulnerable to CVE-2023-34060. According to VMWare, this workaround is safe and does not cause any functional disruptions, not is there a need for concern about downtime, as neither a service restart nor a reboot is required.
Call to Action
For administrators, the call to action is clear — swiftly implement the provided custom script tailored for affected Cloud Director Appliance 10.5.0 versions. VMware acknowledges the urgency of addressing this vulnerability and urges users to stay informed about further updates. In the face of evolving cybersecurity challenges, this collaborative approach becomes essential for safeguarding digital landscapes.
Though, reactive patches are not a thing that provide the best security possible. And the latter is a vital thing for the current threat landscape. Here is the advice on preventing vulnerability exploitation at the beginning.
Measures to avoid vulnerabilities
Vulnerabilities in cybersecurity can pose significant risks to organizations, making it crucial to implement proactive measures to avoid potential threats.
Here are key practices to avoid vulnerabilities:
- Conduct regular cybersecurity training for employees to raise awareness about phishing attacks, social engineering, and other common tactics used by cybercriminals. Educated employees are a crucial line of defense.
- Secure your digital assets. This is a top priority, and that’s where SIEM and SOAR come in. SIEM collects and analyzes security data, while SOAR automates incident response, providing enhanced threat detection and centralized management.
- We suggest implementing both EDR and XDR to combat vulnerabilities. EDR monitors endpoint activity, while XDR offers additional detection and response capabilities.
- Stay informed. Monitor cybersecurity newsletters to see info about the latest vulnerabilities and tactics employed by hackers. This will help with building an effective protection strategy.
- Implement a regular data backup schedule to ensure critical information is protected in the event of a security incident. Store backups offline or on a separate network to prevent them from being compromised in case of a cyberattack.