A group of South Korean researchers from Kunming University published a report detailing how they found the Hive ransomware master key and a method to recover files encrypted with it.
With the help of a cryptographic vulnerability, experts were able to recover the master key of the malware used to create encryption keys.
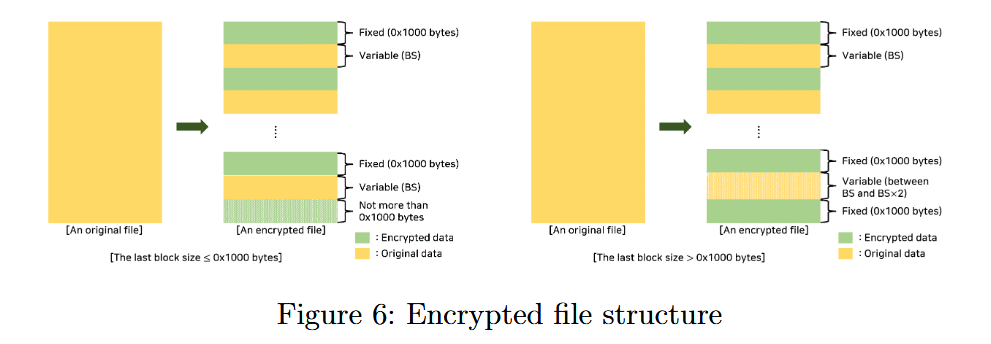
Hive uses a hybrid encryption scheme and relies on its own symmetric cipher to encrypt files, and the researchers were able to determine the way the ransomware generates and stores the master key.
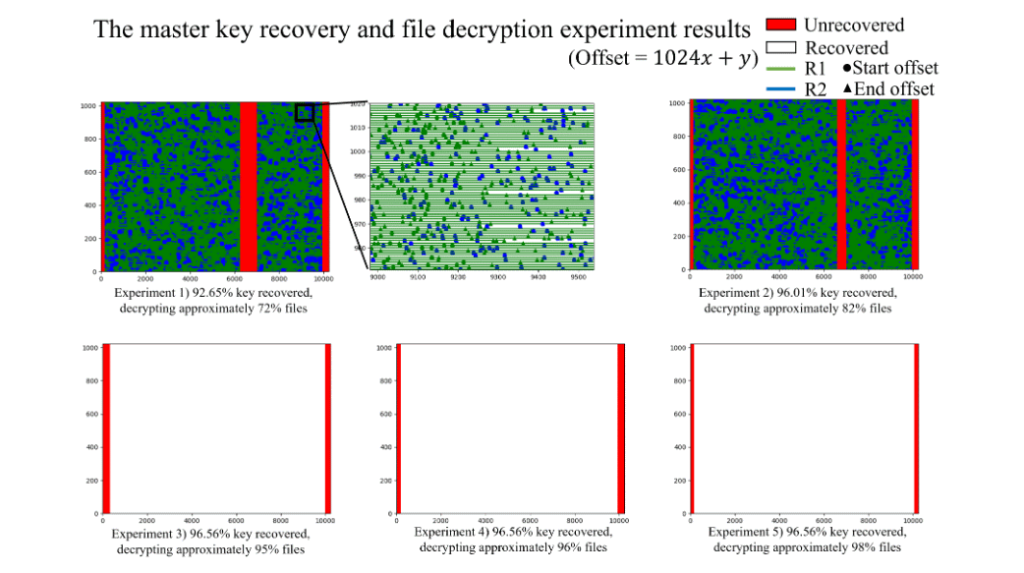
Based on this premise, the experts were able to recover most of the malware’s master key, which was used as the basis for file encryption.
The technique developed by specialists allows recovering about 95% of the master key, and even in such an incomplete form it can be used to decrypt data, recovering from 82% to 98% of the victim’s files.
It is known that specialists from at least two information security companies (Bitdefender and Kaspersky) are currently analyzing the report to find out whether it will be possible to create a free decryptor for Hive based on the findings of Korean researchers.
Initially discovered in June 2021, Hive is offered in an affiliate model that uses a wide range of tactics, methods, and procedures (TTP) to extract data of interest for extortion purposes.
In an alert last August, the FBI noted that Hive is also stopping backup, cybersecurity, and file-copying applications in order to be able to encrypt all targeted files. The ransomware also targets the encryption of the Program Files directories.
Let me remind you that we said that Decryption keys for Maze, Egregor and Sekhmet ransomware were posted on the Bleeping Computer forum, and also that FonixCrypter ransomware stopped working and published a key to decrypt data.