VMware has released a patch for a critical vulnerability in the vCenter Server with a high CVSS score. This vulnerability allows a remote unauthorized user to execute arbitrary code on a target system.
RCE In VMWare vCenter Server Receives a Fix
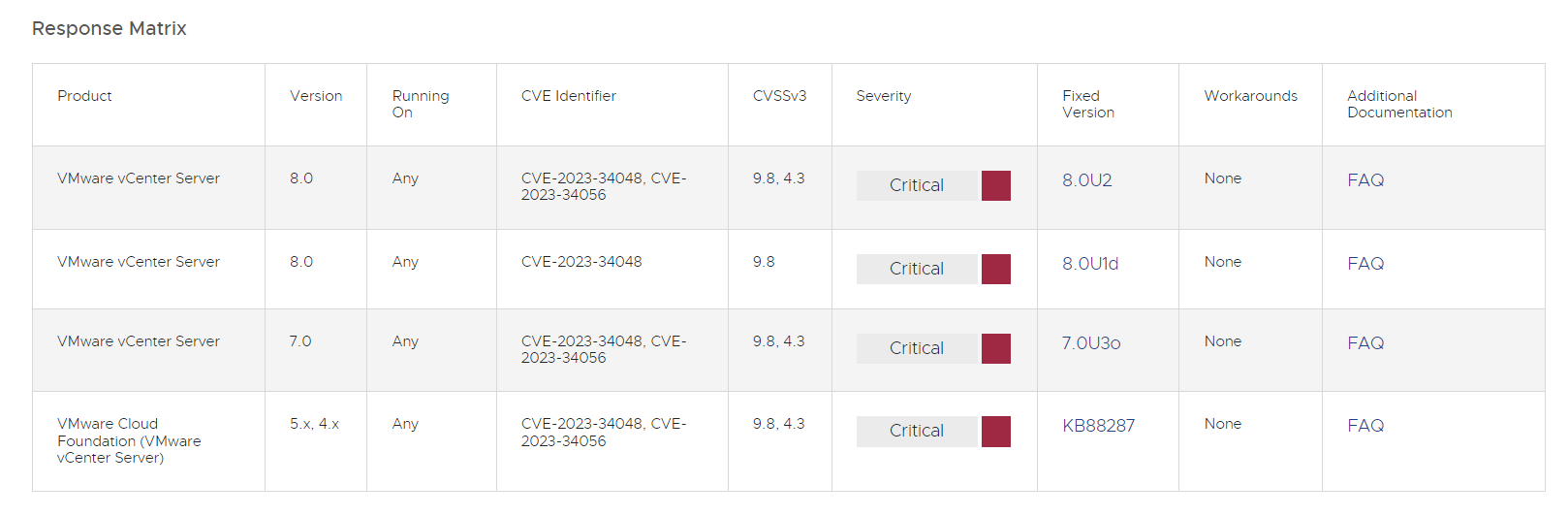
On October 25, 2023, VMware released a patch for a critical vulnerability CVE-2023-34048, which has a maximum CVSSv3 score of 9.8 in the vCenter Server. It allows a remote unauthorized user to execute arbitrary code on a target system. That is, an attacker with access to the network hosting vCenter Server can exploit this vulnerability to gain full control of the target system. Security patches that address this issue are now available through the standard vCenter Server update mechanisms.
In addition, VMware says that “No workaround available”, and administrators should not rely on temporary fixes or alternative measures. Admins should immediately apply the official security patch to address the issue effectively. Moreover, they should take proactive steps to enhance access control. This is especially true for vSphere management components, storage, and network components. Restricting access to only authorized users or systems can help reduce the risk of exploitation.
About CVE-2023-34048 and CVE-2023-34056
CVE-2023-34048 is a critical vulnerability in the VMware vCenter Server that has CVE-2023-34048 has a CVSSv3 base score of 9.8. It allows an intruder to execute arbitrary code on the target system. The vulnerability is caused by an out-of-bounds write vulnerability in the implementation of the DCERPC protocol in the vCenter Server. An attacker can exploit this vulnerability by sending a specially crafted RPC request to the vCenter Server. This request can cause the vCenter Server to write data outside of its allocated memory space, which can lead to arbitrary code execution. An attacker with network access to the vCenter Server could exploit this vulnerability to gain full control over the target system.
Apart from CVE-2023-34048, the latest update further fixes a different vulnerability. That is less dangerous but still concerning. This vulnerability has a CVSS base score of 4.3/10, which indicates moderate severity. Individuals without administrative privileges can exploit it to gain unauthorized access to data that is stored on vCenter servers. So, VMware recommends that organizations treat this issue as an emergency and take prompt action to address it since sensitive data could be at risk. This explains a lot, particularly the fact that the virtualization vendor has provided a patch for vCenter Server 6.7U3, 6.5U3, and VCF 3.x.
Safety Recommendations
Security vulnerabilities in the network infrastructure software is a pet peeve nowadays, as they are uncovered tremendously often. Cisco, VMWare, Oracle – all these names hit the headers with new vulnerability scandals almost every season. And cybercriminals do not hesitate to exploit them, especially once they are described in detail by the developers themselves.
Is it bad that the corporate-grade software is vulnerable? Yes. Is it possible to avoid cyberattacks based on these vulnerabilities? Yes. There is plenty of room for improving the security of your perimeter, and, as saying goes, better safe than sorry.
- Install updates and patches promptly. This tip is the most important because updates and patches often contain fixes for known vulnerabilities. Ignoring this point nullifies the effectiveness of further advice because your system will be vulnerable to attack.
- Use strong passwords and MFA. Strong passwords should be long, complex, and unique to each system. MFA adds another layer of security by asking the user for a one-time password or a confirmation code sent via email or SMS.
- Use Zero trust. Zero trust is a security model that considers all devices and users attempting to access the network to be insecure by default. Under this model, access to resources is allowed only after verifying the identity of the user and device.
- Segment your network. Segmenting your network allows you to divide it into separate parts, each with its permissions. This makes it harder for attackers to access critical systems.
- Keep up with cybersecurity news. The world of cybersecurity is still changing, so it’s essential to stay up to date with the latest trends and threats. Read cybersecurity articles and blogs and subscribe to newsletters and updates from cybersecurity companies.