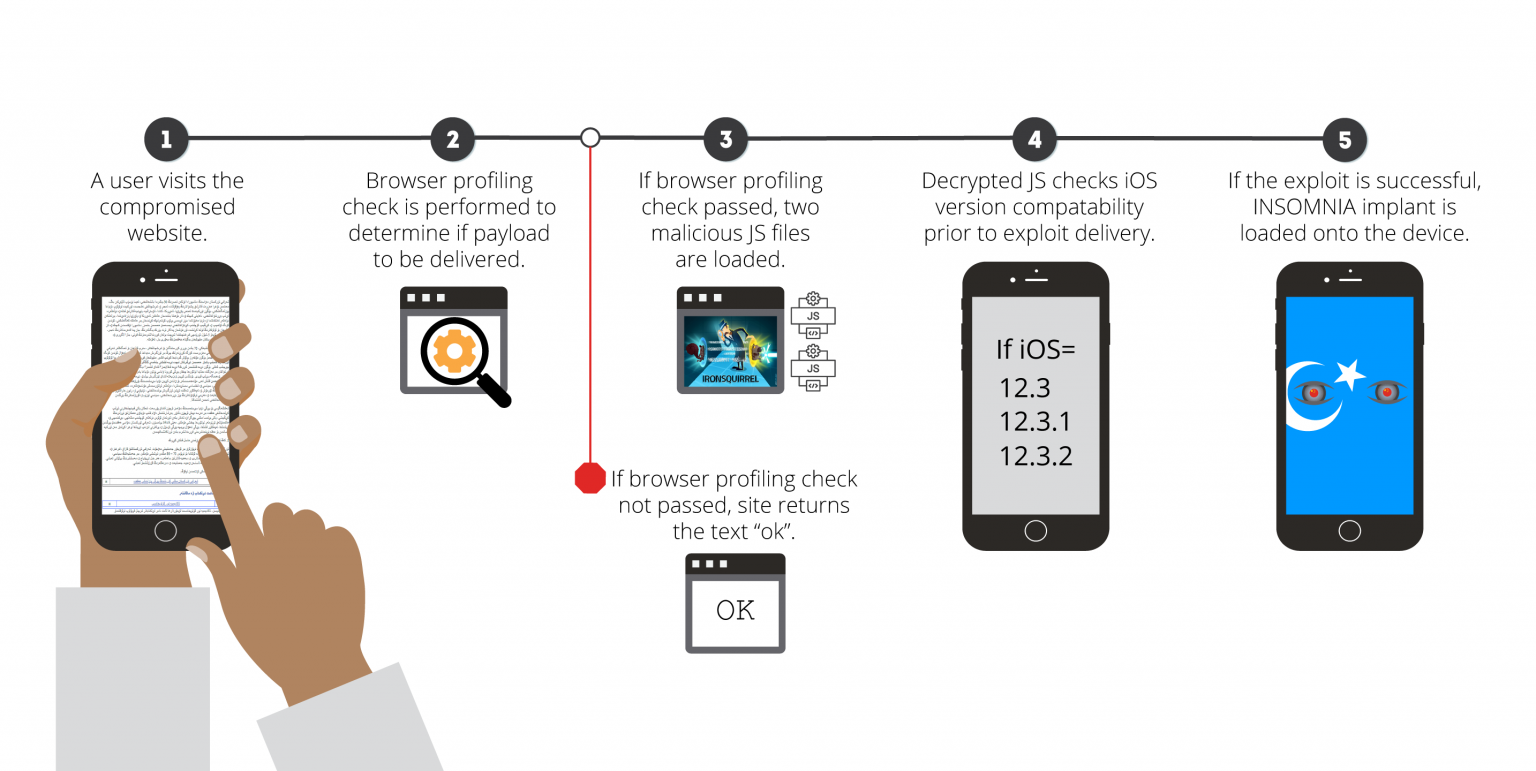
Specialists of the information security company Volexity discovered a new exploit for iOS called Insomnia. According to the researchers, the malware associated with the efforts of the Chinese authorities to trace the Muslim national minority, the Uyghurs, who live mainly in Xinjiang province.
Researchers say that Insomnia works against iOS versions 12.3, 12.3.1 and 12.3.2. Moreover, Apple fixed the vulnerability in the heart of the exploit back in July 2019 by releasing iOS 12.4.
The exploit was actively used against users in the period from January to March 2020. According to the company, it was downloaded to the devices of users who visited a number of Uyghur sites (in particular akademiye[.]Org).
After infection, Insomnia provided root access to infected devices, and attackers used this to steal unencrypted messages from various instant messengers, email, photos, contact lists and location data.
Thus, all iOS users who visited infected with the Insomnia sites were vulnerable to hacking. The exploit could be launched through any browser on the phone, since they all use WebKit. Volexity analysts have confirmed the success of attacks on devices running iOS 12.3.1 through the mobile browsers Apple Safari, Google Chrome and Microsoft Edge.
“This campaign was launched by Evil Eye. It is believed that this is a hacked group sponsored by the Chinese authorities and spying on the Uyghur Muslim minority”, – reports Volexity.
Let me remind you that in the summer of 2019, Volexity and Google discovered another Evil Eye campaign. Then, hackers used 14 vulnerabilities in iOS, which were grouped into five exploit chains and were used against users since 2016. Then it was also a classic attack of the “watering hole” type. Such attacks received their named by analogy with the tactics of predators, who hunt near a watering hole, waiting for prey – for animals that came to drink.
Now, Volexity notes that when Google drew attention to the problem, Evil Eye closed its infrastructure and stopped using old exploits. Instead, in January 2020, hackers switched to Insomnia.
Compared to the 14 exploits that were used before, Insomnia has a number of improvements. So, earlier, attackers could steal victims’ GPS coordinates, photos from the iOS Photos application, contacts, emails from Gmail, as well as messages from Whatsapp, Telegram, WeChat, IMessage and Hangouts. Now, this functionality has been expanded and is working for ProtonMail emails and images sent through the Signal application.
“The inclusion of Signal and ProtonMail [in the list] may indicate that Uyghurs are aware of potential communications surveillance and are trying to use more secure applications to avoid this”, – write the experts.
As in previous cases, Insomnia cannot reliably gain a foothold in the system, so a simple reboot of the device will save it from malicious code. At the same time, the researchers warn that this does not mean that the attackers could not achieve a stable presence on the device at all. Perhaps this just required more subtle manual tuning, after checking the victim.
In general, we live in a time when government surveillance of citizens is not unusual, let’s recall the UAE with the ToTok Arab messenger. Perhaps after quarantine restrictions citizens and more democratic countries will not be against such measures.