Business email compromise attack, or shortly BEC, is a relatively new vector of cyberattacks. Dealing primary damage by exposing potentially sensitive information, it also gives hackers the opportunity to use the email for further attacks. The potential efficiency of these attacks is thrilling, and cybercriminals already apply them to conduct chain attacks. Let’s figure out a precise business email compromise definition, how these attacks work, and how to counteract them.
What is a business email compromise?
The term “business email compromise” mostly says for itself. It is an attack case where an adversary gains access to one or several email profiles that are used by a company for business purposes. Under this attack, hackers posess both personal business accounts and ones that represent the company. The former is mostly used for whaling attacks, while the latter is more useful in external messages. Most often, after succeeding with compromising the account, hackers change password, so the company will not be able to control the account.
Having the control over the corporate email opens a lot of opportunities. Not only it gives the ability to impersonate the company in any conversation, but also allows one to read the past conversations. And while some routine mailing to the clients or contragents may be boring and unclaimed, letters regarding further products, plans and financial situation is a completely different thing. The outcome of the leak of such information is at best worrying.
Business Email Compromise Tools
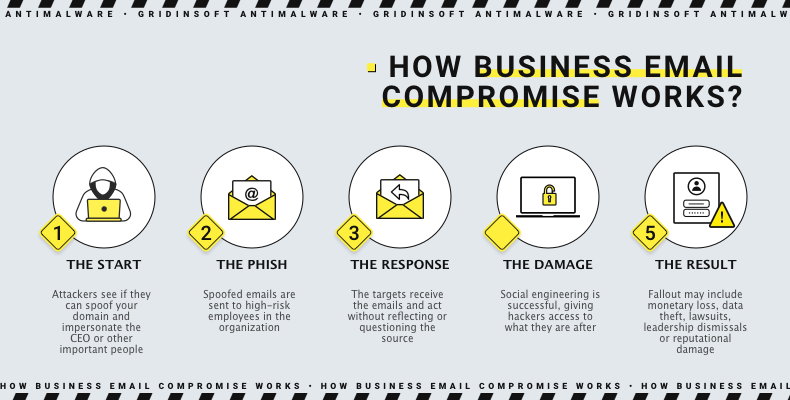
There are not a lot of ways to gain access to the business email. Most often, getting a login and password is a task for a malicious program that is injected into a target computer. Most of the time, there’s no aim at something particular. As soon as hackers get the account, they put it to use on the run. But there are cases where a specific computer is compromised intentionally. In such situations, a deep reconnaissance or even an insider job is used.
Malware type that suits the BEC purposes is obvious – the spyware/stealer malware. These two are mostly identical nowadays, despite their nominally different classification. Spyware or stealer aims at grabbing all login credentials or session tokens they can reach. Some of them – best choices for BEC, as you may suppose – additionally target mailing clients. Those samples are not just taking away the email credentials, they also dump a contact book, making the further work of cybercriminals much easier.
Actions that follow the password compromise depend on the amount of access to the network (and the particular computer) the hackers have. The most obvious way to use the compromised email is to log into it on the computer hackers have direct access to. However, it may expose the IP address and even trigger the alarm, if the mailing client security system tracks system properties. To avoid this, crooks commonly practise deploying additional malware that provides remote access to the needed system. The most often choices for that purpose are backdoors or remote access trojans (RATs). Aside from providing remote access, malware is capable of playing with system settings and processes, so all the malignant actions will be invisible to the machine owner.
Applications for compromised business email
Once the crooks manage to log into the account, the most interesting part of the action begins. I’ve mentioned a couple of possible ways hackers may use the compromised business email. All of them are much more complex, and may include several sub-specimens. Let’s have a look at each one.
Spear phishing
The conjunction of access to past emails and the ability to send new ones opens a new attack vector. When crooks aim at spear phishing, they try to act in a more stealthy manner, as if they change passwords the fact of compromise will be uncovered immediately. A successful spear phishing attempt can provide hackers with a row of other compromised emails, infected devices, or compromised bank accounts. Because of its efficiency, hackers prefer spear phishing over other applications for a compromised business email.
The key action fraudsters do is creating the trustworthy disguise – which is the main difference from a classic email phishing. Having access to past emails, they can pick a topic that will correspond to what victims are waiting for, and use verbal expressions typical for the company. The turning point is a link to a login page or other place, payment information, or so. They lead to a place that hackers need, and people will go on simply because they are not expecting the catch.
Impersonation
Using a compromised business email, hackers can impersonate the company in a pretty convincing manner. It is somewhat similar to spear phishing, but in this case, emails do not contain anything even closely related to the typical company matters. Impersonating the company, crooks may offer random people to install a malicious package, follow the phishing link, or share personal information. Considering the anomaly of such messages from the business emails, the cases of such an obvious spam raise suspicion pretty quickly. Despite that, the “conversion” of receivers into victims is still tremendous – so it may be a suitable option to precisely scam someone.
Whaling
Once getting access to the business email of a company’s top management, hackers can command someone, pretending to be these executives. However, in a more classic variant of whaling scam, crooks impersonate famous persons (or executives) without having such a powerful identity confirmation. Under this disguise, it is possible to create a mess before the business email compromise is uncovered. Asking to send confidential reports, share internal use-only documents or simply disrupting the workflow by some absurd commands – hackers are free to do any of this.
BEC Negative Effects
Based on the possible applications for the compromised business email, you can already guess its negative impact. Main damage here goes to the image of the business. Even if you uncover the incident and reported it – the dirty splash is already on your reputation. Nonetheless, that is nothing compared to the very fact that the company was hacked.
Sure, the scale of damage and possible leak of sensitive information is not always the case when it comes to BEC attacks. However, if you cannot handle the business email properly – how bad will it be with more complicated stuff? The accident-prone company is less likely to gain large contractors and, what is more important, may risk to suffer much more sensible (i.e. money) losses in future.
How to protect against BEC?
BEC attacks were around for quite a while, and for that reason, a lot of counteraction ways were created. They are related to both auxiliary systems application and improving the cybersecurity within the corporate network with passive methods. Though, the best efficiency of all these methods is reached only when all these methods are applied together.
Specialised email security tools
Since email spam is a prevalent way to spread malware these days, this vector of protection obviously pops out. That’s a pretty novice approach towards protecting from phishing email threats. Actually, they’re not separate solutions, but rather add-ons for full-fledged anti-malware software. The key action it does is scanning the incoming emails, exactly their attachments and links. This allows you to detect and dispatch the dangerous item before you can even interact with it.
Content disarm and reconstruction (CDR)
CDR is a toolkit that generally aims at securing the documents you are interacting with. If one has active content in it, CDR will cut it out and give you only static contents of the document. Some CDRs have a system that recognizes the malicious code embedded into the document. Such programs will excise only those parts that trigger the detection. These solution allows to sharply decrease the possibility of malware injection via email – but it does not remove the hazard completely.
Security tools
To be sure that no malicious items are running in the system, it is better to have a dedicated tool. Preventive protection may malfunction, or the threat can simply slip through another way. Properly designed anti-malware software will not let that happen. For securing a personal device you use for business communication, GridinSoft Anti-Malware will fit. Security in corporate networks, however, should be provided with more extensive solutions, like EDR/XDR systems.
Personnel awareness
In organisations, especially large ones, each staff member is a potential attack surface. All security measures I have written above will significantly lose efficiency if there will be such a huge attack surface out of their control. Your personnel should be aware about potential malware injection ways and ready to recognise and react accordingly. Drills and attack imitations may also give a good boost to staff incident response readiness.