According to experts from Zimperium, Android malware FlyTrap hijacks Facebook accounts in 140 countries around the world by stealing session cookies.
Worse, the researchers found that the stolen information was available to anyone who found the FlyTrap C&C server.
Analysts believe the malware has been active since at least this spring.
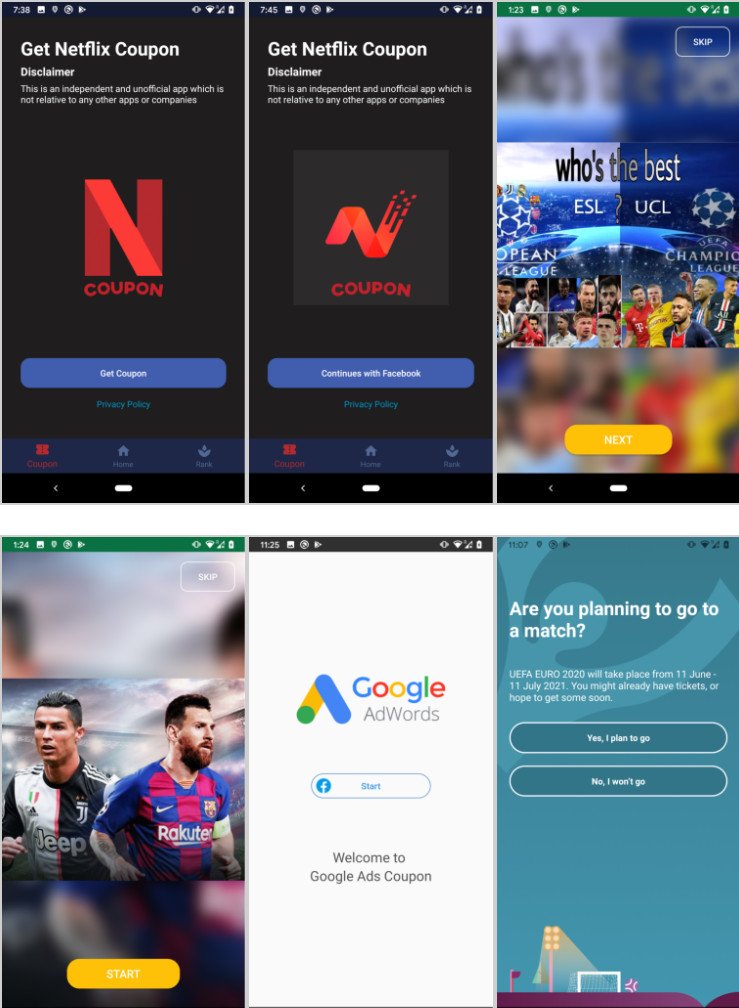
Attackers use decoys distributed through Google Play and third-party Android app stores.
As a rule, such a decoy offers the user free coupons (for Netflix, Google AdWords, and so on) or offers to vote for their favorite football team and Euro 2020 player.
To do this, the victim allegedly needs to log into the application using Facebook credentials, and authentication occurs through the legitimate domain of the social network. Since the malicious apps use real Facebook SSO, they cannot directly collect user credentials. Instead, FlyTrap uses JavaScript injection to collect other sensitive data.
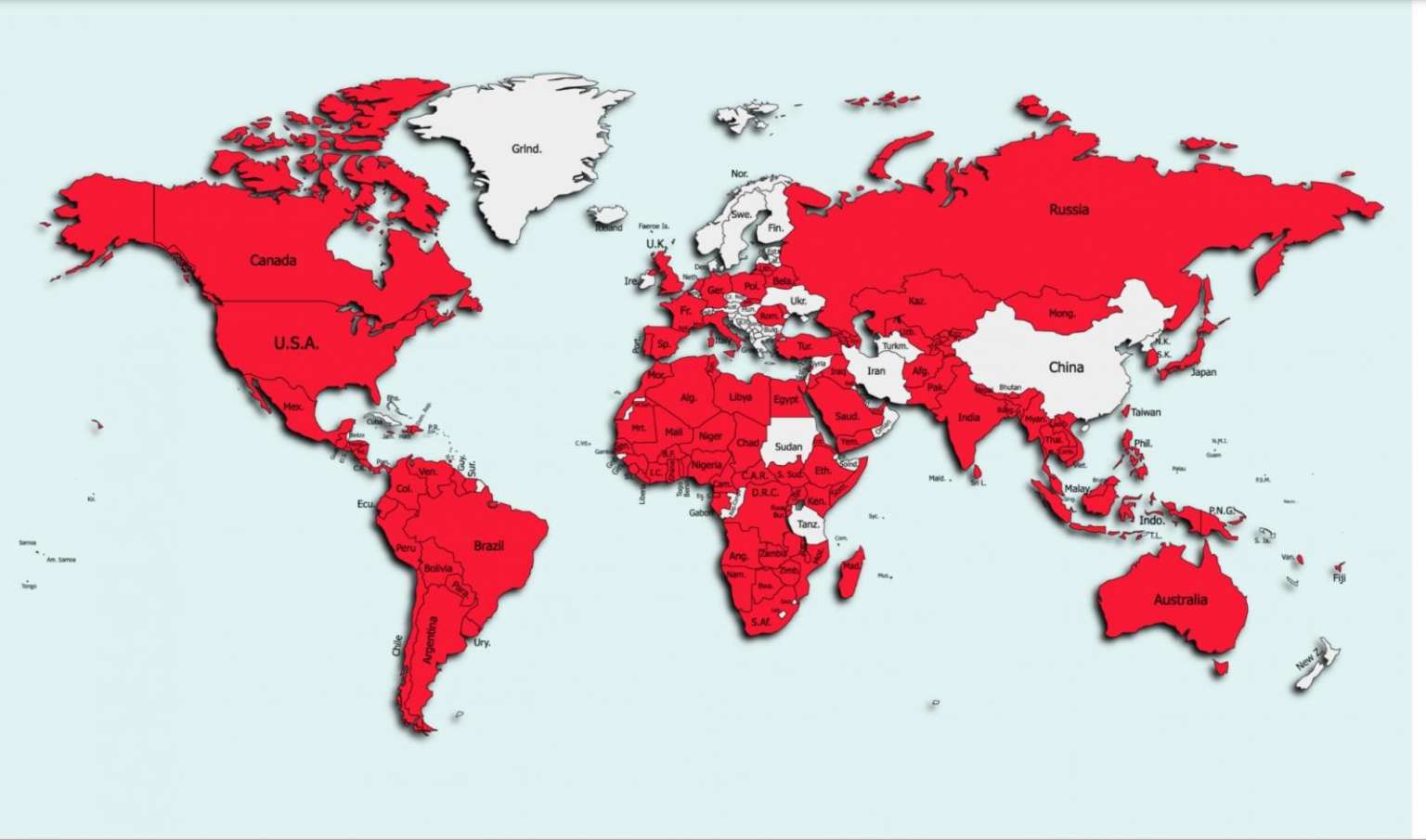
The information collected in this way is transmitted to the attackers’ command and control server. At the moment, more than 10,000 Android users in 144 countries of the world have become victims of this malicious campaign.
The exact data and numbers were extracted from the server of the criminals directly, as the researchers found that anyone could get access to it. According to experts, the FlyTrap C&C server had many vulnerabilities that made it easier to access stored information.
The researchers emphasize that phishing pages that steal credentials are not the only tool used by fraudsters. As the FlyTrap example shows, logging in through a legitimate domain can also be risky.
Let me remind you that I also talked about Alien malware that steals passwords from 226 Android apps.